Latest Blogs

Vulnerability Management: How to Stay Ahead of the Hackers
Introduction
In today’s interconnected digital landscape, cyber-attacks are a constant threat. Cybercriminals are constantly evolving their tactics to exploit vulnerabilities in software and systems. To effectively secure our organizations and sensitive data, proactive vulnerability management is paramount.
Vulnerability management is the process of detecting, assessing, and mitigating vulnerabilities in IT assets. This includes scanning for known vulnerabilities, prioritizing vulnerabilities based on risk, and remediating vulnerabilities in a timely manner.
Proactive vulnerability management can help organizations to:
- Minimize the risk of data breaches and other security incidents.
- Comply with industry regulations.
- Enhance their overall security posture.
Understanding Vulnerability Management
The goal of vulnerability management is to proactively address and reduce the risks posed by vulnerabilities in an organization’s IT infrastructure. It entails a methodical and iterative process that includes finding potential flaws, assessing their effects, ranking them according to severity, and taking the necessary steps to reduce or remove them. To find and validate vulnerabilities, regular vulnerability assessments, penetration tests, and security audits are conducted. Organizations may strengthen their security posture, increase their resilience against cyber-attacks, and protect their vital data and systems from exploitation and compromise by rigorously monitoring vulnerabilities.
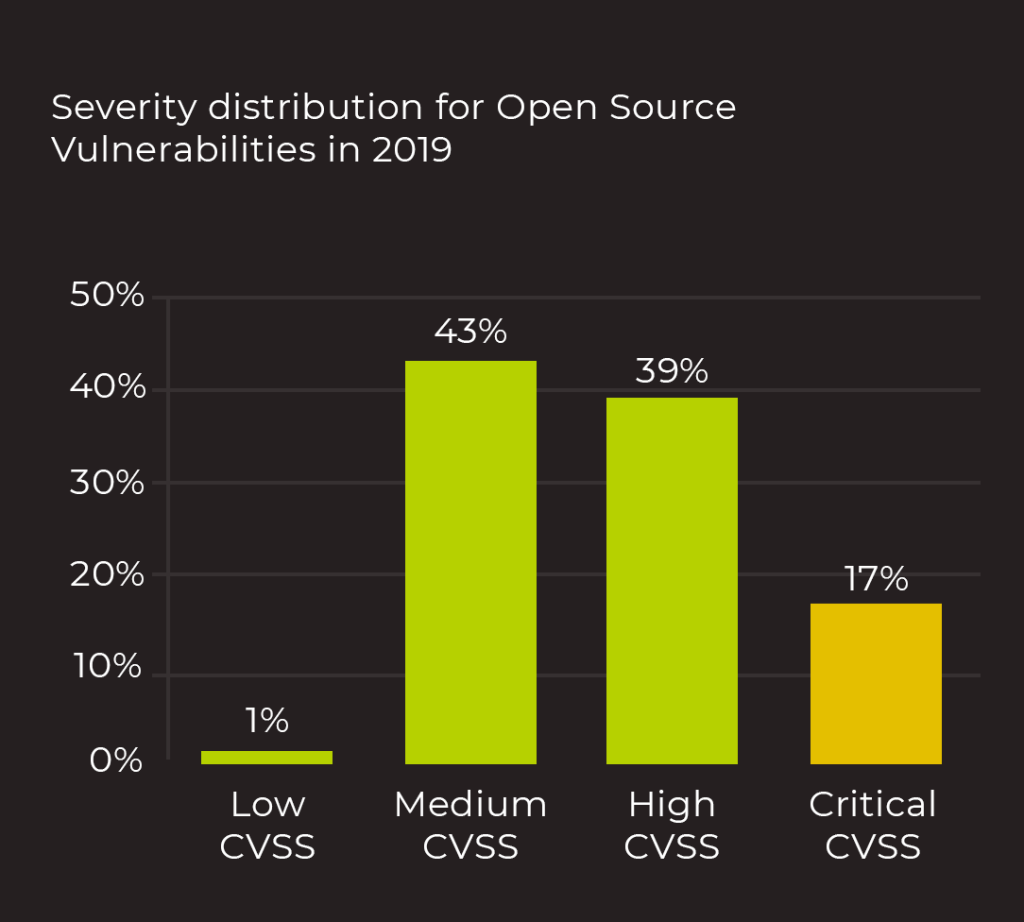
The Importance of Proactive Approach
To stay one step ahead of hackers in today’s fast-paced and constantly changing threat landscape, organizations need to have a proactive vulnerability management approach. Reactive measures are insufficient and risk serious consequences, such as correcting vulnerabilities after an attack. Organizations must have a proactive approach in order to properly protect their systems and data. This entails routinely scanning their infrastructure and apps for vulnerabilities, identifying potential risks using automated tools and methodologies, and swiftly putting mitigation measures in place before attackers can take advantage of them. Organizations may improve their security posture, reduce the probability of successful attacks, and safeguard their sensitive data and important assets by proactively controlling vulnerabilities.
Key Components of Effective Vulnerability Management
- Vulnerability Assessment: The first step in mitigating vulnerabilities is to regularly conduct vulnerability assessments. Organizations can find holes in their systems and rank them according to severity by employing automated scanning technologies.
- Patch Management: It’s crucial to patch vulnerabilities as soon as possible. To ensure that software and systems are promptly updated with the most recent security patches supplied by vendors, organizations should set up effective patch management procedures.
- Risk Prioritization: The level of threat presented by each vulnerability varies. Prioritizing vulnerabilities according to their potential effects on the organization is essential. Use risk assessment frameworks to evaluate and rate vulnerabilities, such as the Common Vulnerability Scoring System (CVSS).
- Continuous Monitoring: Vulnerabilities can arise at any time, and new threats constantly emerge. Install systems for continuous monitoring that keep tabs on organizations and warn them of any potential weaknesses or shady activity.
- Incident Response: A well-defined incident response plan ensures a prompt and well-coordinated reaction in the event of a successful attack. Establishing containment, eradication, and recovery protocols as part of an incident response strategy is a good idea for organizations.
Best Practices for Effective Vulnerability Management
- Regular Vulnerability Scanning: Conduct periodic vulnerability scans to identify and address weaknesses in systems and software.
- Automation: Leverage automation tools to streamline vulnerability management processes, including scanning, patching, and reporting.
- Collaboration: To ensure effective communication and a shared information of vulnerabilities and their impact, encourage collaboration between IT teams, security teams, and business stakeholders.
- Employee Education and Awareness: Invest in ongoing training programs to inform staff on security best practices, such as spotting phishing scams and emphasizing the use of secure passwords.
- Vendor Relationships: For timely updates and patches, keep lines of contact open with hardware and software manufacturers to stay informed of vulnerabilities.
Conclusion
To safeguard themselves against the ever-evolving threat landscape, organizations must continuously monitor their vulnerabilities. Organizations can avoid hackers and protect their systems and data by taking a proactive approach and putting best practices into action. By facilitating effective scanning, detection, and remediation of vulnerabilities, automation solutions can dramatically increase the efficacy of vulnerability management.
To properly handle vulnerabilities and occurrences, you must have a well-defined incident response plan. It explains the actions to be done to ensure a planned and prompt reaction in the case of a security breach or vulnerability exploitation. Following these recommendations can help organizations strengthen their security posture, safeguard sensitive data, and reduce the threat of cyberattacks, minimizing possible harm and monetary losses.
TAGS
- Cyber Crime
- Security Updates
Recent Blogs
By AMSAT July 14,2023
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.










