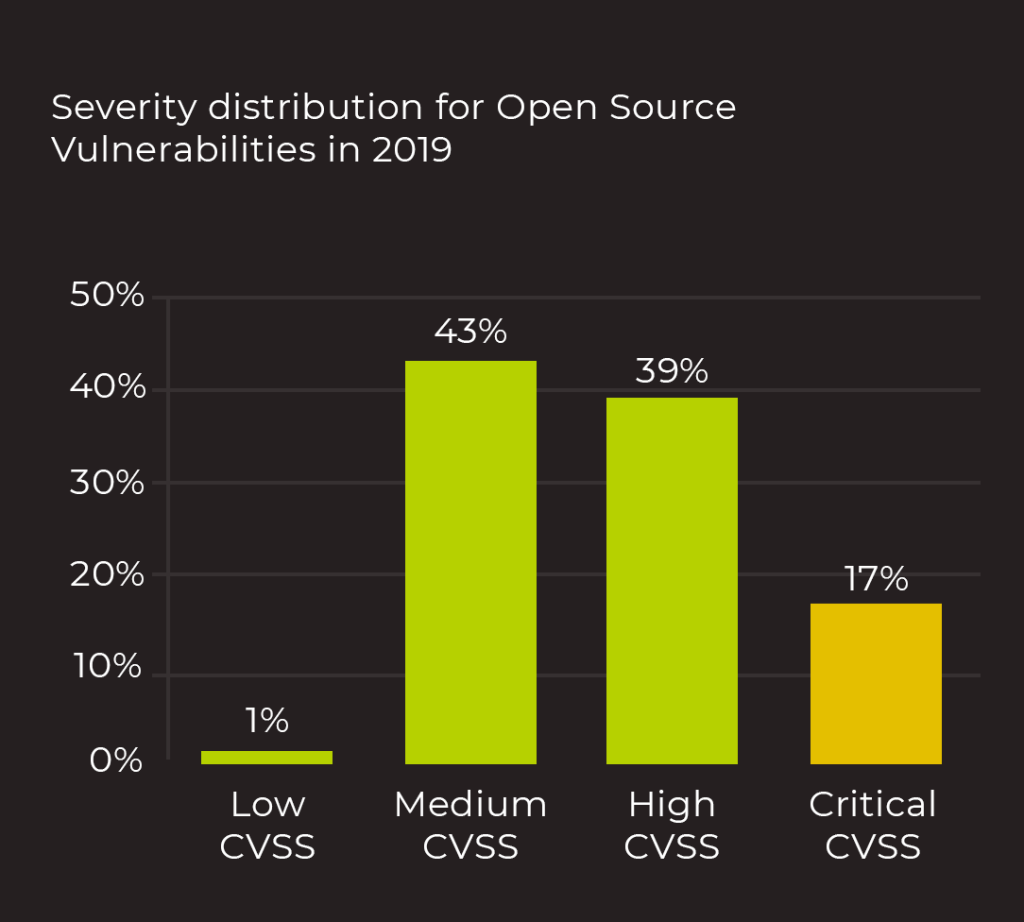
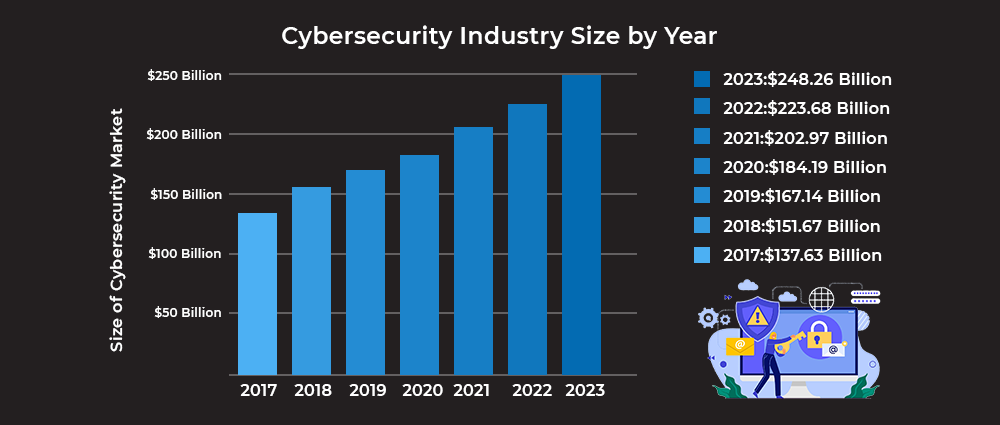
Latest Blogs

By AMSAT Nov 20, 2023
An Insight into Network Security Assessment
Introduction
In today’s fast-evolving digital landscape, visionary business owners consider a secure network a necessity, not an option. No wonder, they give it all to protect their networks from unseen vulnerabilities, waiting to be exploited by threat actors. This is where network security assessments come in; they act as powerful tools to detect and address these flaws before they snowball into serious issues.
Why Network Security Assessment?
A network security assessment is a comprehensive audit designed to safeguard your network, devices, and sensitive data from unauthorized access. It achieves this by exposing weaknesses, gauging defenses, and securing critical assets.

The Two Pillars of Assessment:
There are two main types of network security assessments, each offering unique perspectives:
- Vulnerability assessment: This method pinpoints known weaknesses within your systems, such as outdated software or misconfigured settings. Think of it as a thorough medical checkup for your network.
- Penetration Testing: This simulates an actual cyber-attack, employing real-world tactics like phishing or malware to actively attempt to breach your defenses. It’s like a live-fire exercise, testing your defenses under pressure.
Navigating the Assessment Journey:
Conducting a network security assessment requires a structured approach:
- Inventory Creation: A complete picture of your network is crucial, including all devices, data, and applications. This helps prioritize critical assets and define the assessment scope.
- Information Value Assessment: Not all assets are created equal. Classifying your assets based on their business criticality ensures you focus on the most impactful areas.
- Threat landscape Analysis: Understanding the diverse range of potential threats, both internal and external, is essential for designing a comprehensive assessment strategy.
- Defense Evaluation: Your existing security measures, including firewalls and intrusion detection systems, are rigorously tested to identify any gaps or vulnerabilities.
- Control Enhancement: Based on the assessment findings, concrete steps are recommended to improve your security posture, including patching vulnerabilities and implementing new controls.
- Continuous Monitoring: Security is an ongoing process, not a one-time event. Regular monitoring and reassessments are crucial to adapt to evolving threats and maintain a robust defense.

Conclusion
A network security assessment is an investment in your organization’s future. You can secure your data, operations, and reputation simply by proactively identifying and addressing vulnerabilities.
Partner with AMSAT and build a digital bastion against lurking threats, safeguarding your place in today’s precarious technology landscape.
TAGS
- Network Security Assessment
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.