Latest Blogs

By AMSAT August 30, 2024
Web Application Security Solution
In this day and age of cyber-attacks, you must secure all of your data at all times. We don’t know what sensitive data can be exposed. In order to secure our data, we remember to install firewalls and antiviruses, but forget about securing our web applications and services.
So, how do we go about protecting our web applications?
What is Web Application Security?
The process of protecting our online services, websites, and web applications against malware and cyber threats is known as web application security. These threats target numerous web applications like content management systems like WordPress, SaaS Applications like Zoom, or Administration tools like phpMyAdmin and exploit their code.
When organizations fail to safeguard their web applications, they risk highly sensitive data belonging to their customers open to interpretation and exploitation. This leads to information theft, revoked licenses, and damaged client relationships.
Web Application Security Issues and Solutions
Without proper disinfection, organizations leave their apps open to vulnerabilities, which can lead to a number of problems. But in order to avoid these problems, it is necessary to pinpoint the vulnerable locations and acknowledge ways to mitigate them.
Web Application Vulnerabilities
Here are some of the attack vectors that lead to Web Application Vulnerabilities:
SQL injection
When hackers use harmful SQL code to manipulate backend data, they reveal this SQL code exposure present in your web application. This malicious code helps them disclose all kinds of sensitive information. Leaving this vulnerability unchecked can lead to fatal consequences for your organization like deletion of important info and erasure of sensitive data.
Cross-site Request Forgery (CSRF)
An attack that may lead to unauthorized fund transfers, altered passwords, or data theft is known as Cross-Site Request Forgery. This occurs when a malicious web application forces a user’s browser to execute an unintended action on a site where the user is already logged in.
Remote File Inclusion
A hacker employs this type of attack to remotely inject a file onto a web application server, potentially leading to the execution of malicious scripts or code within the application, along with manipulation or data theft.
Cross-Site Scripting (XSS)
Cross-site scripting is an injection attack aimed at users to gain access to accounts, release Trojans, or change page content. Stored XSS happens when malicious code is directly injected into an application. Reflected XSS occurs when a malicious script is bounced off an application and onto a user’s browser.
Web Application Security Solutions
Web application security is a dynamic, ever-changing field, that adapts as new vulnerabilities and threats emerge. Now, what should we do to mitigate the vulnerabilities listed above? Here are some ways that will work for your organization and work as web application security solutions:
Web Application Firewall (WAF)
Traffic suspected to or known to exploit web application vulnerabilities is filtered by WAFs. They are necessary as new vulnerabilities can emerge rapidly and discreetly, making it challenging for most organizations to spot them on their own.
DDoS Mitigation
These services are positioned between the public internet and servers. They use specialized filtering and high bandwidth capacity to prevent surges of malicious traffic from overwhelming the server.
API Gateways
Sometimes there are shadow APIs that go neglected by strong systems, and API gateways detect these sneaky monsters. They also block traffic targeting API vulnerabilities and assist in managing and monitoring API traffic.
Client-Side Security
This security is necessary as your clients are the most important part of your business. It involves monitoring for new third-party JavaScript dependencies and changes in third-party code, enabling companies to detect cyber-attacks more quickly.
Bot-Management
With the use of AI bots, you utilize machine learning techniques to distinguish between human users and automated traffic, effortlessly prohibiting automated bots from accessing your web services.
Web Application Security Checklist
When you’re attempting to secure your web applications, here’s a checklist you can follow in order to ensure that you add the best web application security solutions:
Gather Information
- Review all applications manually.
- Identify entry points and client-side codes.
- Classify third-party hosted content.
Recheck Authorizations
- Test for path traversals.
- Check vertical and horizontal access control issues.
- Verify for missing authorization and insecure direct object references
Enable Cryptography
- Ensure secure data transmissions.
- Confirm specific data encryption.
- Evaluate for weak algorithms and randomness errors.
Effectively Secure All Your Applications
When you add this checklist to your application development and deployment, you can effortlessly add security to your applications. Additionally, effective tools for attack surface management should also offer a centralized platform to map your attack surface, identify potential security risks, and mitigate those risks with a few clicks. So, ensure that you install all necessary tools and systems before inviting guests to your business.
TAGS
- Cyber Security Updates
- Cyber Security Providers
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT August 22, 2024
Indicator Lifecycle in Cybersecurity
When we talk about indicators, what comes to your mind? Indicators are simply signals that point something out, right?
Similarly, indicators in cybersecurity do the same thing, they don’t necessarily have to be malicious. An indicator can simply be an unknown email in your inbox, it’s not harmful, but it is something that should be investigated. Knowing different kinds of indicators in cybersecurity allows you to use them effectively and track all kinds of attack campaigns accurately.
Key Indicators to Look For

Among all indicators, some are more important than others, they are known as key indicators and those are the ones that our cybers expert analysts look for. These indicators possess the following characteristics:
- Remain constant throughout various intrusions
- Uniquely identify a specific attack campaign
- Differentiate an attack campaign from normal, benign activity
- Correspond to a specific phase in the Cyber Kill Chain
An indicator can be an email, a domain or a malware mutex seen together on multiple occasions. When looking for a key indicator, the chances of seeing a malware mutex and domain together are higher. The goal of our cyber analysts is to identify as many key indicators as possible during intrusion analysis and use them effectively against attackers.
What is Indicator Lifecycle in Cybersecurity

Like the cybersecurity lifecycle, indicators also have a lifecycle that can be used by cyber detectors to hunt all kinds of malware attacks and wrong intentions. The only downside is that the lifetime of these indicators is controlled by the adversaries. If attackers detect that their indicators have been found, they can change the network infrastructure and rebuild the entire malware.
However, before they can do that, our cyber analysts take advantage of the indicator lifecycle and utilize it quite effectively. The indicator consists of three main stages:
Revealed
In this stage, we find an indicator by gathering information and examining intelligence reports, website feeds and our datasets. After detection, we analyze the indicator to ensure its authenticity or in this case legitimacy, relevant to our intelligence requirements and see if we can operationalize it for further threat hunting.
Mature
We reconfigure that indicator to help us in threat hunting. What’s a mature indicator? It’s an indicator that can be utilized by our security tools. We translate the indicator into a form that can be used as a threat-hunting query.
Utilized
In this stage, we use that indicator to reveal other indicators, starting the lifecycle all over again. According to the Courses of Action (CoA) matrix, there are two ways of utilizing a matrix:
Detection
We get to detect our attacker’s current activities generating detection rules.
Discovery
With this CoA, we can discover all of our attacker’s past activities that have been buried before by running a threat-hunting query.
The type of Passive CoA you choose to follow depends on your intelligence tools, requirements, logging capabilities, and the type of indicators you’re going after. With the utilization stage, you go back to revealing new indicators.

FAQs
What are the 5 stages of the cybersecurity lifecycle?
The 05 high-level stages of cybersecurity are:
- Identification
- Protection
- Detection
- Response
- Recovery
What are the 5 Ps of cybersecurity?
These P’s of cybersecurity are the fundamental rules that should be followed by all cyber companies. These include:
- Plan: Establishing clear plans and practices should be a priority in all organizations.
- Protect: Deploy security technologies and controls to defend against cyber threats, such as firewalls and antivirus software.
- Prove: Implement detailed processes that dictate how these security measures can save all kinds of sensitive data.
- Promote: Educate and train people and stakeholders on cybersecurity best practices and awareness to prevent human error.
- Partner: Partner with other organizations and provide them with security tools and solutions that will protect their digital assets as well.
TAGS
- Cyber Security Updates
- Cyber Security Providers
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs
By AMSAT August 20, 2024
Importance of Endpoint Security for Any Organization
In today’s evolving tech landscape, security is more important to organizations than anything. One of the major targets of malware attacks are your consumers at the terminal where your business processes conclude.
So, the most asked question would be: Is this terminal secure?
This terminal is known as the endpoint. Let’s dive into what this endpoint is and why its security is at the utmost priority.
What is an Endpoint?

When talking about an endpoint, we mean any device or server connected to a network. From desktop PCs, laptops and mobile phones, to IoT devices like kitchen appliances, cameras, and thermostats, all devices that may be connected to a network and engage in the sharing and transfer of data are known as the endpoint.
What is Endpoint Security?
We often don’t think about these devices being in danger as we are just used to using them in our daily lives. But what we don’t realize is that these devices are also connected to a server which is part of a huge network containing sensitive information. The phenomenon of securing these endpoints is known as endpoint security.

We secure these endpoints because they also act like the entry point to your organization’s network for cybercriminals, opening the welcoming door to their malicious attacks.
If that’s not enough reason to latch the tight, let’s look at a few more:
Why is Endpoint Security Important?
In the last few years, due to remote working trends, the number of endpoints has doubled.
In recent years, the number of endpoints within businesses has increased. This has been especially the case since the Covid19 pandemic. With more employees working from home, they connect to home and public WiFi, bringing more endpoints to the company’s network. Each of these endpoints is a potential malware-attacking site.
Therefore, locking every door of your modern enterprise is very important.

Businesses are required to protect their data and ensure that they have visibility into advanced cyber threats. In order to minimize these threats and attacks, businesses can install endpoint protection platforms on devices and utilize other tools to mitigate this risk.
How Does End Point Security Works?
Endpoint security operates through an EPP (Endpoint Protection Platform) that continuously monitors for suspicious activities and alerts network administrators of potential breaches. An agent or sensor installed on an endpoint securely streams data to a centralized EPP, allowing for network traffic analysis and, if needed, initiating mitigating actions.

Let’s examine the types of attacks that endpoint data can uncover, enabling an appropriate response:
Malware Installation and Persistence
Malware installation processes differ from those of legitimate software. It has a limited number of methods to maintain persistence in a system.
Attacker Commands
Cyber attackers typically interact with the target system through an operating system terminal.
Before they move laterally, they acquire the credentials of their target.
Lateral Movement
Attackers bring their own set of toolkits with them and often move to other network assets to gather more data on their way to the primary target.
FAQs
Why do we need an endpoint?
Endpoints are crucial as they serve as the primary access points to a network, making them key targets for cyberattacks. Securing endpoints helps protect sensitive data, prevent the spread of threats, and ensure compliance with regulatory requirements
Why is endpoint detection important?
Endpoint detection is vital for early threat identification, preventing literal movement and protecting critical assets in order to mitigate cyberattacks and their impact.
Why is end-user security important?
As the users are the weakest links in a cybersecurity network, their security is of the utmost importance. Protecting the end-users helps prevent unauthorized access, data breaches and the spread of malware in your business.
Why is endpoint security so important to an organization?
Endpoint security is vital because they are also the entry point of malware attacks. Securing endpoints helps prevent breaches, protects sensitive information, and ensures the overall integrity of the organization’s IT environment.
TAGS
- Managed Security Services
- Cyber Security Updates
- Cyber Security Providers
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT August 16, 2024
Top Network Security Threats and Vulnerabilities in 2024
In this rapidly evolving landscape, where changes and advancements are bringing people together and the latest iPhones are the vibe, however, in its midst, network security threat concerns are also valid. A host of new and improved cyber threats emerge daily with even more sophisticated cyber-attacks, including phishing and malware.
A recent study conducted by Cybersecurity Ventures shows that covering cybercrime damages will cost about $10.5 Trillion annually by the end of 2024.
What is a Network Security Threat?

Essentially, network security threats are flaws or weak spots in a network design, development, operation or implementation that can allow unauthorized access to your devices or cause harm to your systems.
In 2024, cyberattacks are the most significantly growing threat for businesses today. Most cybercriminals don’t discriminate between businesses, but if you have a larger and more successful business, then you definitely are more at risk.
Types of Common Network Security Threats
Some of the Top network security threats that organizations are facing today that you need to be aware of are:

Social Engineering
One of the most dangerous types of breaching is social engineering which utilizes the vulnerabilities of humans instead of tech. This makes it all the more dangerous as most infiltrations start with human interactions at the email level.
There are different types of social engineering as well:
Phishing
As mentioned before, hackers interact with people through phishing attacks i.e. emails, social media, or text, masquerading as reliable sources and ask them for sensitive information like social security numbers, bank account details, or passwords.
Spoofing
Like phishing, hackers pretend as someone, but instead of people, here they imitate entire websites to mislead people. For example, they change only a letter on the web address and design a landing page similar to the original website, successfully deceiving people in the process.
Whaling
This kind of phishing is targeted at high officials and executives who possess the company’s most sensitive information. The hackers usually imitate close peers to target them exclusively.
Third-Party Exposure
One of the rising hacking attacks is third-party breaches. As the third parties are not as well-protected as the large corporations they work with, the attackers tend to target them more to get privileged access to their selected organization.
In 2023, 29% of all data thefts occurred due to third-party exposure attacks. This resulted in the leakage of confidential information for many companies and customers.
Mistakes at the Configuration Level
Installing security systems is quite complicated. Even professionally installed systems can give way to one or more errors, leaving the entire system exposed to hackers. This is a major vulnerability as it essentially invites cybercriminals in to steal any information they require.
A configuration issue can be as little as a weak password or as large as installing improper firewalls that will leave the door open for cybercriminals and cause security threats in computer networks.
AI Cyber Threats
Just like how AI has made life easier for software developers, it has also made it quite easy to live for cyber-criminals. Using machine learning methods, these criminals analyze and infiltrate security systems in minutes and leave you vulnerable.
Additionally, they also make attacks automated and frequent, which renders you useless as fixing it takes time and frequent attacks don’t allow any fixtures.
Best Practices for Network Security in 2024
As a large corporation, your security and software must remain updated at all times. It is necessary that you conduct regular software updates, configure robust firewalls, and implement employee cybersecurity training that will allow you to mitigate any and every network security threats and vulnerabilities. Some of the methods are:

Advanced Tools and Technologies
In order to implement robust security methods, you need to ensure that your company has Advanced Threat Protection (ATP) systems and Intrusion Detection and Prevention Systems (IDPS) installed as they are vital tools for identifying and mitigating urgent threats.
Incorporating A Proactive Approach to Network Security
A proactive approach requires regular security audits and continuous monitoring. You also need to decide and implement a comprehensive response plan that will save you from any future security threats.
Protect Your Precious Cargo at the Starting Line With Amsat
With a strong approach and an even stronger security team protecting your sensitive information from breaches, you can rest assured that your data is in safe hands.
TAGS
- Managed Security Services
- Cyber Security Updates
- Cyber Security Providers
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs
By AMSAT April 17, 2024
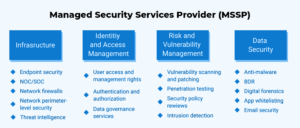
Key points to consider when hiring a Managed Security Services Provider (MSSP)
A managed security service provider (MSSP) offers significant advantages for many businesses. In fact, hiring one can mean you no longer have to worry about risks that an organization is ill-equipped to handle for various reasons, including a shortage of resources or expertise. Seeking a professional provider enables employees to focus on their own key tasks, without taking on the additional responsibility of ensuring security. The following blog post serves as a comprehensive guide to help you identify the key attributes of a top-notch MSSP.
Reputation
Your company’s reputation is pivotal to your business’s success; therefore, it should not be underestimated. It is imperative to ensure that the team entrusted with safeguarding your assets is proficient in their duties and capable of delivering exceptional results.
Asking important questions will help: determine how long a possible provider has been active in the industry and look at feedback they’ve received from other customers. A provider’s status will give you a good idea of their capabilities, and by doing a little bit of research, you can ensure that they’ll be able to deal with your security challenges.
A sound understanding of your business
A good provider should always have a sound understanding of your business and the rules and regulations that must be followed within it. It is important for them to take these guidelines seriously and ensure that key data is secured, allowing your business to continue to protect its customers. Make sure that any potential provider is committed to complying with your business’s specific requirements.
Service level
It’s important to find a provider that offers high quality service. While this may sound too good to be true, MSSPs differ in the service level they provide, and not all will fit your company’s needs. Some providers offer a full incident response system, while others focus exclusively on supervising for intrusions. Some will have knowledge in specific fields of security, which may or may not be valuable to you, depending on what you’re looking for.
Customer support
Customer support is the key element of a quality managed security services provider. In addition to the much-needed support, the level of help provided should also be of the highest quality. After all, you want a provider to explain several procedures and respond to a number of questions. If you’re not getting adequate support from an MSSP, it’s better to look for other alternatives.
Security measures
A competent security provider will always be watchful about new threats, keeping their defense methods up-to-date as security threats change and new technologies evolve. It’s essential that you seek out a quality security provider who is always ahead of the curve, positively impacting your business.
Conclusion
Staying protected is key to the survival of any business, so ensure to conduct thorough research when hiring a new MSSP. No one can take the security of their company for granted; consequently, relying on mediocre MSSPs to save a few hundred bucks will do more harm than good, ultimately contributing to their business’s decline.
TAGS
- Managed Security Services
- Cyber Security Updates
- Cyber Security Providers
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.