Latest Blogs
By AMSAT August 20, 2024
Importance of Endpoint Security for Any Organization
In today’s evolving tech landscape, security is more important to organizations than anything. One of the major targets of malware attacks are your consumers at the terminal where your business processes conclude.
So, the most asked question would be: Is this terminal secure?
This terminal is known as the endpoint. Let’s dive into what this endpoint is and why its security is at the utmost priority.
What is an Endpoint?

When talking about an endpoint, we mean any device or server connected to a network. From desktop PCs, laptops and mobile phones, to IoT devices like kitchen appliances, cameras, and thermostats, all devices that may be connected to a network and engage in the sharing and transfer of data are known as the endpoint.
What is Endpoint Security?
We often don’t think about these devices being in danger as we are just used to using them in our daily lives. But what we don’t realize is that these devices are also connected to a server which is part of a huge network containing sensitive information. The phenomenon of securing these endpoints is known as endpoint security.

We secure these endpoints because they also act like the entry point to your organization’s network for cybercriminals, opening the welcoming door to their malicious attacks.
If that’s not enough reason to latch the tight, let’s look at a few more:
Why is Endpoint Security Important?
In the last few years, due to remote working trends, the number of endpoints has doubled.
In recent years, the number of endpoints within businesses has increased. This has been especially the case since the Covid19 pandemic. With more employees working from home, they connect to home and public WiFi, bringing more endpoints to the company’s network. Each of these endpoints is a potential malware-attacking site.
Therefore, locking every door of your modern enterprise is very important.

Businesses are required to protect their data and ensure that they have visibility into advanced cyber threats. In order to minimize these threats and attacks, businesses can install endpoint protection platforms on devices and utilize other tools to mitigate this risk.
How Does End Point Security Works?
Endpoint security operates through an EPP (Endpoint Protection Platform) that continuously monitors for suspicious activities and alerts network administrators of potential breaches. An agent or sensor installed on an endpoint securely streams data to a centralized EPP, allowing for network traffic analysis and, if needed, initiating mitigating actions.

Let’s examine the types of attacks that endpoint data can uncover, enabling an appropriate response:
Malware Installation and Persistence
Malware installation processes differ from those of legitimate software. It has a limited number of methods to maintain persistence in a system.
Attacker Commands
Cyber attackers typically interact with the target system through an operating system terminal.
Before they move laterally, they acquire the credentials of their target.
Lateral Movement
Attackers bring their own set of toolkits with them and often move to other network assets to gather more data on their way to the primary target.
FAQs
Why do we need an endpoint?
Endpoints are crucial as they serve as the primary access points to a network, making them key targets for cyberattacks. Securing endpoints helps protect sensitive data, prevent the spread of threats, and ensure compliance with regulatory requirements
Why is endpoint detection important?
Endpoint detection is vital for early threat identification, preventing literal movement and protecting critical assets in order to mitigate cyberattacks and their impact.
Why is end-user security important?
As the users are the weakest links in a cybersecurity network, their security is of the utmost importance. Protecting the end-users helps prevent unauthorized access, data breaches and the spread of malware in your business.
Why is endpoint security so important to an organization?
Endpoint security is vital because they are also the entry point of malware attacks. Securing endpoints helps prevent breaches, protects sensitive information, and ensures the overall integrity of the organization’s IT environment.
TAGS
- Managed Security Services
- Cyber Security Updates
- Cyber Security Providers
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs
By AMSAT Sep 19,2023
Types of Endpoint Application Isolation and Containment Technology
In today’s digital world, securing endpoints such as computers, mobile devices, and servers has become increasingly important.
Organizations around the world consider endpoint security to be a major challenge, with application isolation and containment technology being one key feature of this aspect. This technology plays a critical role in preventing malware, data breaches, and unauthorized access to sensitive information.
Containment applications, which is another primary aspect of this technology, play a critical role in isolating and neutralizing threats before they can spread to other parts of a network. This blog will delve into various types of endpoint application isolation and containment technology and how they can enhance security.
1. Sandboxing Technology
Sandboxing is a security method that isolates applications in a controlled environment to prevent them from spreading malware to the rest of the system. Sandboxes limit applications’ access to system resources and data, providing a safe space for them to execute.
Sandboxing is particularly effective against zero-day exploits, which are attacks that exploit vulnerabilities in software that the software vendor is not aware of. When a suspicious file or application is opened in a sandbox, its behavior is carefully supervised. If any malicious activity is spotted, the sandbox can terminate the application, preventing it from damaging the host system.
2. Virtualization-Based Isolation
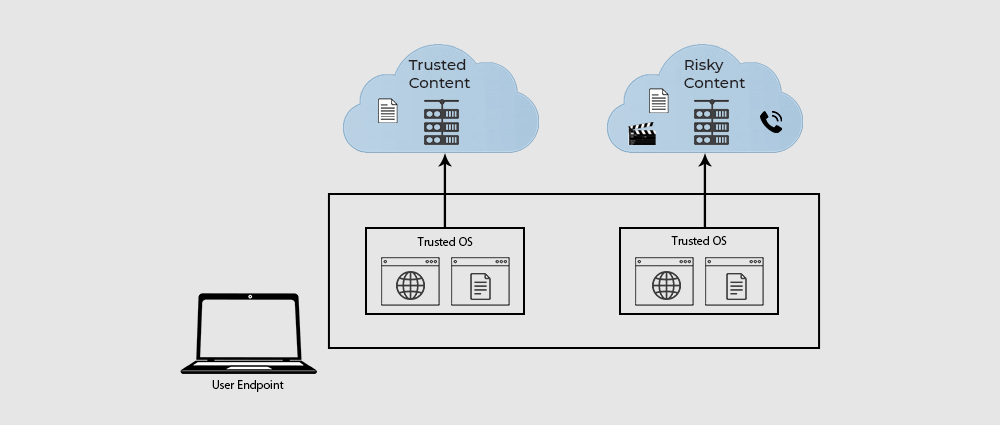
A security technique that isolates applications in separate virtual machines (VMs) or containers, virtualization-based isolation provides a higher level of security than traditional sandboxing. It prevents malware from escaping one container and contaminating others or the host system.
Each virtual machine or container is a separate environment with its own resources and operating system. This prevents programs running in several VMs or containers from interacting with one another or the host system. Even if one application is infected, this isolation stops malware from spreading to other applications.
Enterprise environments frequently use virtualization-based isolation to separate sensitive workloads and applications. For instance, a business might use virtualization-based isolation to isolate its financial systems from its customer relationship management (CRM) apps by running each in a different virtual machine (VM) or container. This helps prevent malware that might attack CRM software from compromising the banking applications.
3. Containerization
A technique of isolating applications in lightweight containers that share the host operating system’s kernel, containerization makes containers more efficient than virtual machines (VMs). Containers also have their own file systems, libraries, and resources, which further isolates them from each other and the host system.
Because containerization enables quicker and more effective application deployment and scalability, it is a common strategy in DevOps and microservices contexts. Since containers may be easily moved between several cloud providers, they are also ideally suited for cloud computing.
To maintain security, it’s crucial to configure containers properly. Containers are vulnerable to some attacks because they share the same kernel as the host system. For instance, the entire host system might be compromised if a malicious container is successful in exploiting a kernel vulnerability.
4. Application Sandboxing on Mobile Devices
On mobile devices, application sandboxing is a security technique that isolates each app in its own environment, limiting its access to device resources. This prevents malicious apps from accessing sensitive user data or interfering with the core functionality of the operating system.
Mobile operating systems like iOS and Android use sandboxing to protect users from malware and other security threats. Sandboxing is also used to prevent apps from crashing or interfering with each other.
In addition to sandboxing, mobile operating systems also use permission systems to control how apps access device resources. When an app requests access to a resource, such as the camera or location services, the user is prompted to approve or deny the request. This gives users control over their privacy and security.

5. Network-Based Isolation
A security approach that isolates applications or devices on separate network segments, network-based isolation is different from endpoint isolation, which separates applications on individual devices.
Network-based isolation is commonly used in enterprise settings to protect critical systems and sensitive data. By isolating these resources on a separate network segment, security cab be better maintained sue to limited potential impact of a breach.
Conclusion
Endpoint application isolation and containment technology is a crucial component of contemporary cybersecurity methods. Sandboxing, virtualization-based isolation, containerization, mobile app sandboxing, and network-based isolation are some of the technologies that can help secure against a variety of risks, from malware to unauthorized access.
While each technology has its own strengths and weaknesses, a layered approach that combines multiple techniques can provide strong security for endpoints. Amid an ever-evolving digital landscape, keeping abreast of these technologies and employing best practices is key to protecting sensitive data and systems.
TAGS
- Endpoint Security
- Containment Technology
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT Aug 10,2023
Protect Your Business with the Top Endpoint Security Vendors in the UAE
The UAE’s business landscape is increasingly reliant on technology, making it a prime target for cyber-attacks. In recent years, there has been a surge in the adoption of cutting-edge cyber security solutions in the UAE, as businesses recognize the importance of protecting their sensitive data and ensuring operational continuity.
A robust endpoint security strategy involves not only safeguarding individual devices, but also the intricate web of network connections they comprise. To address this need, the market is teeming with a diverse array of endpoint security vendors, each offering a distinctive set of solutions tailored to the varying requirements of businesses, regardless of their scale.
Among the most reputable and sought-after endpoint security vendors in the UAE are Kaspersky, McAfee, Trend Micro, Sophos, and Bitdefender. These industry leaders have earned their status by delivering innovative technologies that empower businesses to mitigate risks, thwart cyber threats, and ensure the resilience of their digital infrastructure.
In an era where the consequences of cyber breaches can be far-reaching and devastating, the significance of robust endpoint security cannot be overstated. By partnering with esteemed vendors and leveraging their comprehensive suites of protective measures, businesses in the UAE can fortify their defenses, repel malicious intrusions, and confidently navigate the intricate cyberspace terrain.
When choosing an endpoint security vendor, it is important to consider the following factors:
- The size and complexity of your business
- The types of data you need to protect
- Your budget
- The level of support you require
Once you have chosen a vendor, you will need to implement their solution and ensure that it is properly configured and managed. This will help to protect your business from the latest cyber threats.
Here are some of the features to look for in an endpoint security solution:
- Malware protection: This should include real-time scanning, anti-virus, and anti-spyware capabilities.
- Ransomware protection: This should include features to prevent ransomware attacks and to decrypt files that have been encrypted by ransomware.
- Intrusion detection and prevention: This should identify and block unauthorized access to your endpoints.
- User behavior analytics: This can help to identify malicious activity by users.
- Reporting and analytics: This should provide you with visibility into the security posture of your endpoints.
Here are some tips for protecting your business with endpoint security:
- Keep your endpoint security solution up to date with the latest definitions and signatures.
- Implement a layered security approach that includes other security measures, such as firewalls, intrusion detection systems, and data encryption.
- Train your employees on how to identify and avoid phishing emails and other social engineering attacks.
- Have a plan for responding to a cyber-attack.
To learn more about endpoint security and how to protect your business, visit the websites of the top endpoint security vendors in the UAE. You can also contact a security solutions provider to discuss your specific needs.
Conclusion:
Endpoint security is a crucial line of defense in the United Arab Emirates (UAE)’s dynamic and technologically advanced business environment. The likelihood of cyber threats like malware, ransomware, and data breaches rises as the digital world becomes more connected. Endpoint security emerges as a crucial precaution for navigating this complicated landscape, requiring a comprehensive and multifaceted solution.
It is crucial to choose a reliable provider who can offer a complete endpoint security solution. Established suppliers provide a variety of cutting-edge technologies and strategies that can protect businesses from the wide range of growing cyber dangers. By putting these solutions in place, businesses can proactively identify possible threats and take action to stop them, protecting sensitive data, ensuring business continuity, and maintaining consumer trust.
In a world where cyberattacks can have far-reaching consequences, businesses in the UAE must prioritize endpoint security to strengthen their digital infrastructure and ensure a resilient operational landscape.
TAGS
- Cyber Crime
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs
By AMSAT Aug 7,2023
The Importance of Endpoint Security in the UAE
Cybersecurity is a growing concern in today’s rapidly changing business landscape, with companies all over the world taking appropriate steps to safeguard their data and assets from malicious actors. Like any other country in the world, cybersecurity companies in the United Arab Emirates (UAE) have also seen a significant increase, especially in the last few years, making the country highly susceptible to looming cyber threats.
Since the UAE’s digital infrastructure is vast and complex, spanning sectors such as finance, energy, healthcare, and transportation, cybercriminals find it easier to exploit it for a wide variety of targets. The UAE’s strategic location also makes it a prime target, as cyberattacks could have regional and even global repercussions.
In 2021, the UAE was ranked as the 10th most targeted country in the world for cyberattacks. These attacks resulted in significant financial losses and disruptions to businesses and government agencies.
Several endpoint security companies in the UAE offer advanced solutions to protect businesses from cyber threats and ensure the safety of their digital assets. One of the most common ways that cyber attackers target businesses in the UAE is through endpoint devices. Endpoints are any devices that are connected to a network, such as laptops, desktops, mobile phones, and tablets.
Endpoint devices are a prime target for cyberattackers because they often contain sensitive data, such as customer information, financial records, and intellectual property. Additionally, endpoint devices are often not as well-protected as other parts of a network, making them easier for attackers to exploit.
That’s why endpoint security is so important for businesses in the UAE. A comprehensive endpoint security solution can help to protect devices from a wide range of threats, including malware, ransomware, phishing attacks, data breaches, and zero-day attacks.
Endpoint Security Compliance in UAE
The UAE is a rapidly growing digital economy, but this growth comes a heightened risk of cyber threats. In order to protect their sensitive data and comply with the UAE’s rigorous regulatory framework, organizations operating in the country must prioritize stringent endpoint security measures.
By diligently adhering to endpoint security compliance in the UAE, businesses can not only fortify their digital perimeters but also contribute to the overall resilience of the UAE’s digital ecosystem. This helps to create a secure and trustworthy environment for both local and global stakeholders.
Endpoint security solutions typically include a variety of features, such as:
- Anti-virus and anti-malware protection
- Firewalls
- Intrusion detection and prevention systems
- Device control
- User behavior analytics
The best endpoint security solution for your business will depend on your specific needs and requirements. However, all businesses in the UAE should take steps to protect their endpoints from cyberattacks.
The UAE must take a diversified strategy to improving endpoint security in order to protect digital assets. Software must be updated often in order to prevent vulnerabilities from being exploited by hackers. Using strong passwords and two-factor authentication together strengthens defense against unauthorized access and adds an extra layer of security.
It is essential to educate personnel about the constantly changing world of cyber risks. They are equipped to recognize potential threats and take caution thanks to regular training and educational programs. By implementing a variety of defensive tools, such as firewalls and intrusion detection systems, a layered security strategy further fortifies defenses and builds a robust barrier against future breaches. Individuals and organizations in the UAE can greatly improve their endpoint security posture by following these guidelines.
Some of the leading endpoint security solutions in the UAE include McAfee, Symantec, Kaspersky, Bitdefender, and Trend Micro. The following are some of the leading endpoint security solutions in the UAE:
These solutions offer a variety of features and benefits, so you can choose the one that best meets your needs.
If you’re looking for help with endpoint security in the UAE, contact a security solutions provider. They can help you assess your needs and recommend the best solution for your business.
Here are some of the most common endpoint security threats in the UAE:
- Malware: Malware is software that is designed to harm a computer system. Malware can steal data, install backdoors, or disrupt operations.
- Ransomware: Ransomware is a type of malware that encrypts a victim’s files and demands a ransom payment in order to decrypt them.
- Phishing attacks: Phishing attacks are emails or text messages that are designed to trick the recipient into providing personal or financial information.
- Data breaches: Data breaches occur when sensitive data is stolen from a company or organization.
- Zero-day attacks: Zero-day attacks are attacks that exploit vulnerabilities in software that the software vendor is not aware of.
Conclusion
The UAE places utmost importance on protecting endpoints with strong security measures. The growing frequency of cyberattacks against small local firms highlights the urgent need for an all-encompassing endpoint security strategy. By implementing the best practices and recommendations described in this blog, you can protect your company from online threats. By giving endpoint security top priority, you not only protect your endpoints but also strengthen your enterprise’s overall resilience in the face of escalating cyber threats.
TAGS
- Endpoint Security
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT July 27,2023
How to Prevent Data Loss with Endpoint Security
Introduction
Endpoint security is the practice of protecting devices that connect to a network, such as laptops, desktops, and mobile devices. It is a critical component of any organization’s overall security posture, as it can help to prevent data loss, malware infection, and other cyberattacks.
There are many different aspects to endpoint security, including:
Device management: This involves keeping devices up to date with the latest security patches and software.
Application control: This allows organizations to control which applications can be installed and run on endpoints.
User behavior analytics: This helps to identify and prevent malicious activity by users.
Data loss prevention (DLP): This helps to protect sensitive data from being leaked or stolen.
DLP policies are an important part of endpoint security because they can help to identify and protect sensitive data. This data can include credit card numbers, social security numbers, and intellectual property. DLP policies can also help to prevent users from accidentally or intentionally sharing sensitive data with unauthorized individuals.
In addition to DLP policies, there are other ways to prevent data loss with endpoint security. These include using strong passwords and multi-factor authentication; encrypting sensitive data; and backing up data regularly.
By offering comprehensive endpoint security services, organizations can help to protect their data from a variety of threats.
How Endpoint Security Can Help Prevent Data Loss
Endpoint security can help prevent data loss in a number of ways. First, it can help to identify and protect sensitive data. This is done by using DLP policies to classify sensitive data and then monitor for unauthorized access or exfiltration of that data.
Second, endpoint security can help to prevent malware infection. This is done by using antivirus and anti-malware software to scan devices for malicious code. Endpoint security solutions can also help to block malicious websites and attachments.
Third, endpoint security can help to prevent unauthorized access to devices. This is done by using firewalls and intrusion detection systems to monitor network traffic and identify suspicious activity.
Best Practices to Prevent Data Loss
Below are some best practices every security team should follow in its DLP strategy and when considering DLP tools.
Identify and Classify Sensitive Data
Understanding the different types of data you have is the first step in successful data preservation. Your data repositories will be searched and reported on by data discovery and data classification technology, giving you access to the content you need to safeguard.
As information is modified, created, stored, or delivered, data categories can be updated. However, security measures must be in place to stop users from changing category levels. For example, lowering data categorization should only be possible for privileged users.
Assess Internal Resources
Organizations must determine the necessary DLP skills and activities, such as risk analysis, data breach response, reporting, data protection regulations, and DLP training and awareness, before they can create and implement a DLP plan. Some governmental restrictions require businesses to seek outside experts or engage in-house data protection specialists.
For example, the General Data Protection Regulation (GDPR) of the European Union has regulations that apply to businesses that sell goods. A data protection officer (DPO), who will be in charge of compliance audits and DLP performance monitoring, must also be designated in accordance with the GDPR.
Implement in Phases
Data loss prevention (DLP) is a long-term process that is most effective when implemented incrementally. This means that you should start by prioritizing the most important data types and communication routes, and then add additional modules or components as needed.
Your priorities should be based on a thorough risk analysis and data inventory, which should be performed at the beginning of the process.
Establish Data Management Policies
Data loss prevention (DLP) policies should be created to manage different data and communication types. Government regulations set standards for DLP policies, which include handling sensitive data and recovery strategies in case of data loss. DLP personnel can then customize policies based on the organization’s needs.
DLP systems use pre-configured rules or processes based on different regulations, such as GDPR or HIPAA. One example of a DLP software and enforcement package is McAfee DLP Prevent, which monitors outbound channels and offers options to resolve potential security breaches. Machine learning technologies automate these checks to ensure reliable security.
Train Your Employees
Data loss prevention (DLP) depends on employees understanding and following security policies and procedures. Training and education, such as classes, online training, occasional emails, and posters, can help employees understand the importance of data security and how to follow recommended DLP best practices.
If you are interested in learning more about how to prevent data loss with endpoint security, please contact us today. We would be happy to discuss your specific needs and help you implement a solution that is right for your organization.
Conclusion
Endpoint security is a vital pillar of any comprehensive cybersecurity strategy for organizations. By effectively implementing endpoint security measures and adhering to industry best practices, companies can significantly reduce the risk of data loss and safeguard their critical information from potential threats. Protecting sensitive data is paramount in today’s digital landscape, where cyberattacks are ever-evolving. Through our expert services, we aim to guide and support organizations in fortifying their endpoints, securing networks, and bolstering their overall cybersecurity posture.
Reach out to us today, and our team of specialists will be delighted to engage in a tailored discussion, addressing your specific needs and devising a customized solution suitable for your organization’s unique challenges.
TAGS
- Cyber Crime
- Endpoint Security
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT July 24,2023
How to Choose the Right Endpoint Security Solution for Your Organization
Endpoint security is the practice of protecting devices that connect to a network, such as laptops, desktops, smartphones, and tablets. Since these devices are often the first point of entry for cyberattacks, it is important to have a strong endpoint security solution in place.
When choosing an endpoint security solution, you must consider a number of factors, including the size and complexity of your organization, your budget, and your specific security needs. You will also need to consider the features that are important to you, such as threat detection and prevention, EDR capabilities, malware protection, patch management, and user education.
It is important to choose an endpoint security solution that is right for your organization’s needs. By doing your research and considering all of your options, you can find a solution that will help to protect your devices and your data from cyberattacks.

Here are some of the most important factors to consider:
Threat detection and prevention: The primary function of an endpoint security solution is to detect and prevent threats. Look for a solution that leverages advanced technologies like machine learning, artificial intelligence, and behavioral analysis to identify and stop threats before they can cause harm.
EDR capabilities: EDR (endpoint detection and response) solutions offer more advanced capabilities than traditional antivirus software. They can collect and analyze endpoint data to identify and respond to threats in real time.
Malware protection: A good endpoint security solution should provide protection against a wide range of malware, including viruses, Trojans, and ransomware.
Patch management: Endpoint security solutions should also include patch management capabilities to help you keep your software up to date and secure.
User education: Employee education is an essential part of any endpoint security strategy. Make sure your employees know how to identify and avoid phishing emails, malicious websites, and other threats.
In addition to these factors, you should also consider the following:
The size and complexity of your organization: If you have a small organization with a few endpoints, you may be able to get away with a simpler endpoint security solution. However, if you have a large organization with a large number of endpoints, you will need a more robust solution.
Your budget: Endpoint security solutions can range in price from a few hundred dollars to several thousand dollars per year. You need to choose a solution that fits your budget and your security needs.
Your specific security needs: What are your specific security concerns? Do you need protection against a particular type of malware? Do you need to comply with specific regulations? Make sure the endpoint security solution you choose can address your specific needs.
Once you have considered all of these factors, you can start to evaluate different endpoint security solutions. There are a number of reputable vendors that offer endpoint security solutions, so you should have no trouble finding one that meets your needs.
Here are a few of the most popular endpoint security vendors:
- CrowdStrike
- Fortinet
- McAfee
- Palo Alto Networks
- Sophos
Endpoint security is a critical component of any organization’s cybersecurity strategy. Endpoints are often the first point of entry for cyberattacks, so it is important to have a strong endpoint security solution in place.
When choosing an endpoint security solution, there are a number of factors to consider, including the size and complexity of your organization, your budget, and your specific security needs. You will also need to consider the features that are important to you, such as threat detection and prevention, EDR capabilities, malware protection, patch management, and user education.
In addition to these factors, there are a number of additional tips that can help you choose the right endpoint security solution for your organization. These tips include:
Get recommendations from industry experts. Talk to other organizations in your industry and see what endpoint security solutions they use. This can be a great way to get insights into the different solutions available and to learn about the experiences of other organizations.
Read reviews. There are a number of websites that offer reviews of endpoint security solutions. These reviews can provide you with valuable information about the different solutions available, such as their features, capabilities, and pricing.
Test drive the solution. Most vendors offer free trials of their endpoint security solutions. This is a great way to try out a solution and see if it meets your needs. You can also use the trial period to test the solution’s compatibility with your devices and your network.
By following these tips, you can choose the right endpoint security solution for your organization and help to keep your data safe.
Conclusion
No matter which vendor you choose, make sure you do your research and read reviews before you make a decision. Endpoint security is an important part of any organization’s cybersecurity strategy, so you need to make sure you choose the right solution for your needs.
TAGS
- Endpoint Security
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT Dec 01, 2021
Why Your Business Needs Endpoint Security
Cyberattacks are on the increase and the years ahead are likely to be worse. If you are a business owner of a company of any size, you should not take your cybersecurity for granted.
On the whole, business leaders barely think much about securing their networks from virtual attacks until the situation spirals out of hand. Some organizations may take several months to identify data breaches study, which implies that, following a breach, threat actors have more time to distribute sensitive information before consumers, businesses and others begin to assuage the damage.
Endpoint devices are one of the most susceptible components of a business network, something even IT specialists tend to ignore. In view of the rise in date breaches over the last few years, organizations should focus on endpoint security for complete protection of their vital business assets.
Endpoint protection of enterprise systems is a useful way of managing software deployment and executing IT security operations procedures. Endpoint security, however, does much more than safeguard a network from malware, and IT managers can use it for many operation supervising positions and data backup policies.
Management Features
The unified management feature of endpoint security software makes deployment easy. Delivery of security capabilities across the principal infrastructure within an enterprise system network is automatic, providing an IT manager with centralized control over remote workstations. Endpoint solutions bring into line security updates across endpoints so that new security applications are sourced automatically. Identification of security threats is done with client-side SaaS response.
Data Loss Protection (DLP)
Given that most companies now depend on data-centric approaches for management operations, data loss protection (DLP) is a priority for IT security strategies. Endpoint security solutions prevent deliberate or inadvertent data loss owing to systems breach or fiasco. The most effective endpoint solutions will regulate access breaches that are triggered by
credentialed users such as employees, implying organizations can block files transmitted through email, instant chat, or Internet upload. Endpoint encryption is a further assurance that conceals data on a laptop so that access by third parties cannot be achieved.
Internet security that’s offered with endpoint security SaaS is crucial to a company looking to lessen the risk of systems threats by viruses and malware. As the best security technology for preventing emergent threats, endpoint security identifies and removes threats immediately. Endpoint security also examines server-based client email, chat, and IM communications applications used in ordinary work processes for risks to IT infrastructure.
Resource Usage
Enterprise resource planning (ERP) is often part of an endpoint security plan. The efficacy of ERP in security when compared to other IT security solutions specifies that endpoint solutions save expenses in terms of regulating data losses, installation across networks, and with updates. Recovery time to restarting operations is nearly nil, making endpoint security SaaS a foremost choice for ERP plans.
User Ease
When gaging adoption rates by managers and client users, endpoint security solutions outdo other IT security choices. Ease-of-use features cut IT resource demands, as well as technical requirements such as automated updates, deployment, and Active Directory incorporation. However, endpoint security software has some restrictions. Based on the hardware system, installation of the Web-based management console onto a server rather than a PC usually means a rapider time to operations. Custom endpoint security solution SaaS packages are created to highlight the exclusive operational needs of a company, yet may need extra backup or data loss prevention tools to meet file requirements.
Endpoint Security as Solution
Vindicating the return on investment to integrate an endpoint security solution into a current enterprise system needs measuring its efficacy in vulnerability management, and the calculation of the actual financial value of assets.
Abuses of designated user access credentials, intellectual property theft, and employee misappropriation of internal communications with personal devices can lead to expensive litigation and recovery situations. Endpoint security software is the best possible system of implementing IT policy. With endpoint security SaaS, businesses can now secure assets and block malware from damaging operations and eventually profits.
About AMSAT
AMSAT’s state-of-the-art infrastructure and effective systems help organizations defend against present and future threats, which can be tailored to specific needs of our clients. The AMSAT team includes some of the leading security practitioners in a broad set of cybersecurity capabilities. This covers areas of application and network security, analysis, pro-active, legal, reactive and forensic services. AMSAT also provides the largest and most efficient Security Operations Center in Pakistan where cybersecurity experts are monitoring events on 24/7, helping organizations implement robust, consistent and stable cybersecurity practices.
TAGS
- Endpoint Security
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs
By AMSAT Aug 28,2021
An Outline of Endpoint Detection and Response (EDR)
What is EDR?
Endpoint detection and response, or EDR, is a unified endpoint security solution that spots and examines suspicious activities on hosts and endpoints, using a high level of automation to enable security teams to swiftly recognize and respond to threats.
EDR systems provide five basic functions, which include:
Actively overseeing endpoints and gathering data from activity that may hint at a threat;
Performing assessment of collected data to detect any known threat patterns;
Generating an automatic response to all known threats to either eliminate or contain them;
Automatically informing security staff that a threat has been detected;
Making the most of investigation and forensic tools to carry out research on recognized threats.
Why is Endpoint Detection and Response important?
The security landscape is continuously changing, with looming threats of viruses, malware, ransomware and more. To meet this growing threat, real-time collection and detection of possible irregularities becomes all the more important.
These challenges are exacerbated by the highly mobile workforce—thanks largely to the Covid pandemic. When workers connect remotely, endpoints being used for access to a company’s digital assets are generally owned by an employee. These devices may be shared on networks by the employee’s family and therefore may be infected with malware without the knowledge of the employee.
By utilizing EDR, a company can help meet these challenges by:
- Finding and blocking executables that could carry out malicious acts;
- Preventing USB devices from being used for unlawful data access or downloading private or protected information;
- Blocking fileless malware attack methods that could infect endpoint devices;
- Safeguarding from zero-day attacks, and stopping them from inflicting harm
How does EDR work?
EDR works by supervising traffic on the network and endpoints, gathering data pertaining to security issues into a major database for later evaluation, and enables reporting and probing into threat events.
All EDR solutions are not created equal – the extent of the activities they carry out can differ from vendor to vendor. Major components of a typical EDR solution include data collection agents, central hub, response automation, and forensics and analysis.
Kaspersky Lab: the bonafide security partner
A number of security companies, large and small, claim to provide that they are the official partners of Kaspersky Lab, a Russian multinational cybersecurity and anti-virus provider. But the fact is just the opposite. The company is a world leader in developing and selling endpoint security, antivirus, internet security, password management, and other cybersecurity products and services.
About AMSAT
AMSAT’s state-of-the-art infrastructure and effective systems help organizations defend against present and future threats, which can be tailored to specific needs of our clients. The AMSAT team includes some of the leading security practitioners in a broad set of cybersecurity capabilities. This covers areas of application and network security, analysis, pro-active, legal, reactive and forensic services. AMSAT also provides the largest and most efficient Security Operations Center in Pakistan where cybersecurity experts are monitoring events on 24/7, helping organizations implement robust, consistent and stable cybersecurity practices. Our solutions are ideally geared for the medium to large enterprises, critical infrastructure and law enforcement and sensitive organizations. AMSAT also provides access to the best-of-breed cybersecurity solutions covering areas such as Endpoints, Data Flow Analysis and Anomaly Detection, Intrusion Detection and Prevention, Application and Network Firewalls, Wireless Security, Cloud Security, Penetration Testing, and SWAT/Tiger and Forensic Teams.
TAGS
- Cyber Crime
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT Sep 01, 2021
Increased Ransomware Attacks Lay Bare the State of Cybersecurity
Every few years a slew of major threats, including APTs, IoT Security and Cloud Security, draw the attention of security vendors, start-ups, media and board meetings. Today, it can be safely said that Ransomware is dominating the discourse, particularly after so many high-profile events have been part of the news cycle, as well as several stories on healthcare providers being wronged by such attacks.
Ransomware is not a new phenomenon, and nor are its delivery systems; even demanding ransom isn’t new. The technical novelty presented in Ransomware events, encoding files on a hard drive, can’t be considered very sophisticated. However, despite handling a threat that we had several years to prepare for and defend ourselves from, Ransomware is amazingly popular because it works, and it is very lucrative for the threat actors.
In earlier threats, the security industry has confronted challenges of new technical competences emanating from cybercriminals. In the heyday of banking malware, new ground-breaking features such as HTML injections and Man-In-The-Browser were presented by their developers, causing vendors to struggle in detecting fake activities. APTs emerged as a major threat because they were able to dodge conventional cyber defence principles, which focused on the perimeter and had no “strategic depth” of finding threat actors after they were already in the systems. IoT and Cloud security required new methods as the settings that they sought to defend were quite different from the settings that security solutions were intended for. In contrast, ransomware has none of these challenges.
The term ransomware was initially used to describe a specific type of malware that encoded the victim’s hard drive and demanded a ransom to decode the infected files. Once companies started to alleviate the threat by applying more demanding backup policies, the attack loosened and began to include data exfiltration as well. Whether a ransom is wanted for data decoding or the deterrence of the data’s publication, there are similar technical challenges of delivering an effective attack, as well as foiling it.
The key delivery technique of ransomware is through spear phishing. A malware-affected document is sent as attachment to one of the company’s employees, which is triggered once the document is opened. This type of delivery technique has been part of the default method of most APT groups since they came into the limelight in almost 2010. While the industry has generally focused on the standard change that it had to experience in order to alleviate APTs, shifting from safeguarding the organization’s perimeters to securing the organization’s internal networks as well, many vendors specifically dealt with spear phishing as well. Despite directly dealing with these threats as well as the abundant time that has passed since they were first detected – ransomware establish that this issue has not been solved in several organizations. Attack vectors from over a decade ago are still tremendously successful, even when they are executed by cybercriminal groups and not developed countries.
The attack vector is not the only component of the attack. When data exfiltration is used to hold the organization for ransom, we again meet a method that has been disseminated by APTs. The act of exfiltration is a vital part of these age-old threats and should hypothetically be spotted by the solutions aimed to alleviate it. The fact that many ransomware events include the publication of internal data from files and documents demonstrates that even after over a decade, the security business fails to defend many organizations.
It’s not claimed that the industry fails to halt attacks on a technical level. We only hear about the successful attacks and possibly many more attacks are stopped compared to those that were successful. Nevertheless, the fact that so many large and prestigious businesses fall victim to an attack that in many cases does not represent any new technical challenge suggests that there are still many issues that need to be fixed. The fiasco is not technical in nature, but a business one.
One of the main challenges of cybersecurity is the fact that attacks can come in several forms and trajectories. Numerous bases need to be covered in order to be secured. Cybersecurity has become very multifaceted, in terms of applying solutions to shield one own’s organization that we have authorizations now to ensure everything is applied properly.
If we really want to defend businesses all together, not just specific customers, to ensure a safe cyberspace for all, the security business needs to stop focusing on the trending topics and begin working on solving the real problems. Until these issues are resolved, ransomware and malware will continue to inflict damage and illustrate just how bad the overall security situation is.
TAGS
- Cyber Crime
- Security Updates
- Ransomware Attacks
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT july 05,2021
How to Build End-to-End Security for 5G Networks
The advent of 5G presents unmatched opportunities for organizations, particularly those competing in today’s constantly growing and highly competitive digital ecosystem.
5G brings a phenomenal surge in mobile broadband and high-reliability as well as ultra-low latency (URLLC). The ensuing growth of new, highly responsive applications, rich media streaming, and more will entirely transform networks. And that’s just the beginning. The expansion and distribution of cutting-edge high band millimeter-wave (mmWave) 5G will hasten the development of smart infrastructures, boost the automation of manufacturing settings, and provide the ultra-high density required to control new computing environments.
Nevertheless, as organizations embrace 5G networks and services to enable digital innovation across new network limits, they are also presenting new risks. And part of the 5G challenge is that there are few security solutions on the market intended to keep up with 5G-boosted networks. We already see some environments—not just super-high performance data centers, but new edge compute milieus and even remote workers on 5G-enabled devices—being badly protected. For example, millions of remote workers are now being secured with little more than a VPN connection. Without a security plan in place, these enterprises will be unable to secure themselves against the next generation of malware designed to harness the speed and magnitude of 5G and take advantage of the patchy and thinly deployed security systems currently in place.
5G Security Challenges
There’s no doubt that everybody wants to ensure that security controls don’t overshadow the reason they are embracing 5G in the first place. Security systems not intended for 5G settings can slow applications, introduce dormancy issues, and affect the user experience of workers and customers. Luckily, 5G includes several integral security capabilities that can help. But we must be wary not to over rely on them. No enterprise moving critical data, applications, and workflows across their network or relying on business applications to link to important resources should ever consider 5G as their only source of protection against cyber threats or the deliberate misuse of infrastructure and services. An extra layer of security discernibility and control designed for the realities of a 5G network is essential.
But this is about much more than just purchasing a fast firewall. 5G is going pervasive, meaning we will see it organized everywhere across the circulated network—in LANs, WANs like SD-WAN, data centers, cloud platforms, and cloud-based services as well as endpoints and IoT devices. It will not just pervade IT but will play an important role in OT as well. From a security viewpoint, each of these settings already has its challenges. Endpoint security has grown from old-style antivirus software to providing complete protection from sophisticated malware and evolving zero-day threats.
End-to-end Security and High Performance
Dealing with this challenge begins by converging networking and security into an integrated solution—a process known as security-centric networking—to produce a security plan that is not just highly flexible and adaptive but that can be widely deployed. By intertwining security into the core of the network, security systems will not only be able to develop and adjust to digital innovation efforts but do so at 5G speeds. This enables an end-to-end method that can deliver vital security while keeping low dormancy and high performance. But attaining this requires a platform method that can provide steady protection to any user on any device in any location.
The job of a security platform is to be deployable anywhere, in any form factor, while offering steady functionality across and between edges. And for 5G, virtual platform instances should not only be able to scale up and out to meet performance demands, but physical devices need to include improved processing power, so security never becomes a blockage.
The first benefit of an integrated platform method is that it enables single-pane-of-glass visibility, steady policy distribution and enforcement, centralized threat intelligence collection and association, and orchestrated response to recognized threats. It also lets security follow data, workflows, and transactions end-to-end, rather than handing off security as data moves from one area to the next, important in a world where enterprises run on applications.
But maybe the most critical value of a platform is that it enables true automation. 5G-enabled threats will far overtake the capacity of data analysts and systems engineers to spot and respond. Automated systems are integrally quicker than humans. And when improved with things like machine learning and AI, they can also spot, examine, and respond to threats right off the bat, shutting them down mid-attack, even at 5G speeds.
A Secure 5G Ecosystem
Though 5G is opening a world of opportunities for digital business, it’s only the tip of the iceberg at the moment. 6G is impending, and many of the ways this new functionality will affect organizations haven’t even been conceived yet. But all this will only be possible if security is a vital part of the solution. Enterprises need to start transitioning now to a global security platform that can scale as networks evolve and extend to the farthest reaches of the network. By merging security and networking functionality into a combined, expansive, and flexible platform, organizations can prepare now to support the next generations of high-performance, hyperconnected systems and devices their users will demand and on which their future relies.
TAGS
- Endpoint Security
- Endpoint Protection
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.
Latest Blogs

By AMSAT Aug 28,2020
Dealing with cyber-threat: a complex challenge
Across the globe, organizations in various sectors, both public and private, now openly recognize that cyber-attacks are one of the most widespread and gravest risks they encounter.
Given the risks organizations around the world face with regard to the security of their data, dealing with cyber-threat has become a complex challenge. Much of the existing focus is on security and compliance, as companies – subject to growing amounts of legislative, corporate and regulatory requirements – prove they are handling and securing information appropriately.
Since the information security landscape is constantly evolving, private and public sector organizations find it hard to believe they could be a target for cyber-attacks. This approach needs to change, as it’s best to be proactive rather than reactive. At the same time, relying on defense is no longer viable, as the threat actor bent on wreaking harm to an organization will be unrelenting in their objective. This results in public and private sector organizations getting to know what is going on around them so that they can recognize when an attack has occurred or when an attack is on the cards. Intelligence and the intuition that it brings is at the core of next generation of information security.
The importance of cybersecurity
Why should security figure at the top of every organization’s top priority list? Why should senior management of every small and large organization be concerned about cybersecurity?
The answer: The digital world in which business is conducted is susceptible and prone to being attacked. Digitization brings with it boundless opportunities for innovation. It still has a long way to go before becoming a fully protected system that is set to control and regulate itself. Decision-makers ought to ensure that all systems in their company abide by the latest high-security protocols. Employees, particularly not so tech-savvy, must also be competent in basic cyber-security etiquettes. For example, everyone needs to know how to recognize a phishing email and how to isolate it, while informing the proper authority, both internal and external.
Without the right security strategy, you might be in for an irreparable damage for your organization. Even with the sturdiest controls in place, an organization would do well to bank on those controls to be tested. Threat attackers know how to find weak spots and take advantage of them, opening holes up that bring down robust systems. The solution lies in being offensive rather than defensive, and practicing the essential security tasks that will keep most of the threats at bay.
TAGS
- Cyber Crime
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.





