Latest Blogs
By AMSAT Nov 13, 2023
Top 5 Open-Source Host-Based Intrusion Detection Systems
In today’s interconnected world, protecting our systems from cyber threats is key. Host-based intrusion detection systems (HIDS) play a vital role in this defense, unceasingly monitoring and examining system activity to detect and alert on malicious behavior. While commercial HIDS solutions are available, open-source alternatives offer a cost-effective and customizable option. This blog will delve into the top five open-source HIDS that can significantly improve your cybersecurity posture.
Here are the five open-source host-based intrusion detection systems to help you secure your organization.

Short for for Open-Source Security Event Correlator, OSSEC is a well-known and highly regarded solution free and open-source host-based system. With roughly 6,000 monthly downloads, OSSEC is characterized by its scalability and multi-platform feature because it runs on Windows, different Linux distributions, and MacOS.
This tool, which can be compared to Wazuh, enables you to perform log analysis, file integrity checking, policy supervision, rootkit finding, and active response using both signature and anomaly discovery methods. It provides important insight into systems operations in order to identify irregularities.
Tripwire is a free and open-source host-based detection system. Developed by Tripwire, this tool is known for amazing capabilities to ensure data integrity. It also helps system administrators to spot alterations to system files and informs them if there are tainted or tampered files.
If you wish to install it on your Linux host, you can just use the apt-get or yum utilities. During the installation, you will be required to add a mandatory passphrase, which should ideally be a complex one. Once installed, you’ll need to initiate the database and you can easily begin your checks.
This is another open-source monitoring solution for integrity monitoring, incident response, and compliance. Wazuh offers security discernibility into the Docker hosts and containers, overseeing their behavior and spotting threats, flaws and irregularities.
The open-source solution uses incongruity and signature finding approaches to detect rootkits as well as carrying out log analysis, integrity checking, Windows registry monitoring, and active response. Wazuh can also be used to oversee files within Docker containers by focusing on the consistent volumes and bind mounts.
Another key open-source intrusion detection system, Samhain helps you check file integrity, oversee log files, and spot veiled processes. Simple to install, this runs on POSIX systems; all one needs to do is download the tar.gz file from the official web page and install it on your system. Samhain projects come with wide-ranging and thorough documentation, providing centralized and encoded monitoring capabilities over TCP/IP communications.
Designed and maintained by Doug Burks, Security Onion is a free and open-source IDS composed of 3 components: full packet capture function, intrusion detection systems that correlate host-based events with network-based actions as well as many other utilities. The tool is the perfect solution if you wish to establish a Network Security Monitoring (NSM) platform easily and quickly—thanks largely to its friendly wizard.
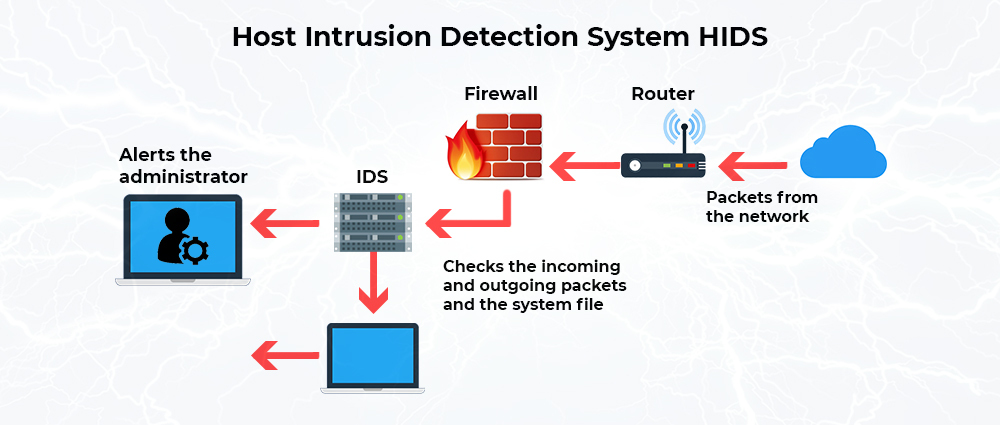
Choosing the Right HIDS
The choice of HIDS depends on several factors, including the size and complexity of your environment, your specific security needs, and your technical expertise. For organizations with limited resources, Samhain or Tripwire might be suitable due to their lightweight nature.
For larger environments, OSSEC or Wazuh offers a broader range of features and scalability. Security Onion is a great choice for organizations seeking a comprehensive security solution with a unified view of network activities.
Conclusion
Open-source HIDS offer a powerful and cost-effective alternative to commercial solutions, providing a robust layer of security for your systems. By carefully evaluating your needs and selecting the right HIDS, you can considerably improve your cybersecurity posture and secure your valuable data assets from unauthorized access and malicious activities.
TAGS
- Intrusion detection systems
- Security Updates
- Cyber Security
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.









One thought on “Top 5 open-source host-based intrusion detection systems”