Latest Blogs

By AMSAT July 31,2023
The Latest Cyber Threats Facing the UK and How to Stay Safe
The UK is facing a growing number of cyber threats, from ransomware attacks to data breaches. In 2022, there were over 2.7 million cyber-related frauds in the UK, with a total value of over £2.3 billion. These cyber threats are becoming increasingly sophisticated and can have a devastating impact on individuals, businesses, and the government. To its credit, the National Cyber Security Agency in the UK works diligently to safeguard the nation’s critical infrastructure and protect against cyber threats.
The latest cyber threats facing the UK include:
- Ransomware: Ransomware is a type of malware that encrypts a victim’s files and demands a ransom payment in order to decrypt them. Ransomware attacks have become increasingly sophisticated, and they can now target businesses of all sizes.
- Data breaches: Data breaches are incidents in which sensitive personal or financial data is stolen from a company or organization. Data breaches can have a devastating impact on victims, as they can lead to identity theft, financial fraud, and other problems.
- Phishing: Phishing is a type of social engineering attack in which attackers send emails or text messages that appear to be from a legitimate source. The emails or text messages often contain links or attachments that, when clicked, install malware on the victim’s computer.
- Business email compromise (BEC): BEC is a type of fraud in which attackers impersonate a legitimate business email address in order to trick victims into sending them money or sensitive information. BEC attacks have become increasingly common in recent years, and they have cost businesses billions of dollars.
What AWS Cyber Security Does
AWS Cyber Security provides a comprehensive set of services that help organizations protect their data and applications in the cloud.
AWS offers a wide range of security services that help organizations protect their data, applications, and infrastructure. These services include:
- Identity and access management (IAM): IAM helps organizations manage user permissions and access to AWS resources.
- Network security: AWS offers a variety of network security services, such as firewalls, VPNs, and intrusion detection systems.
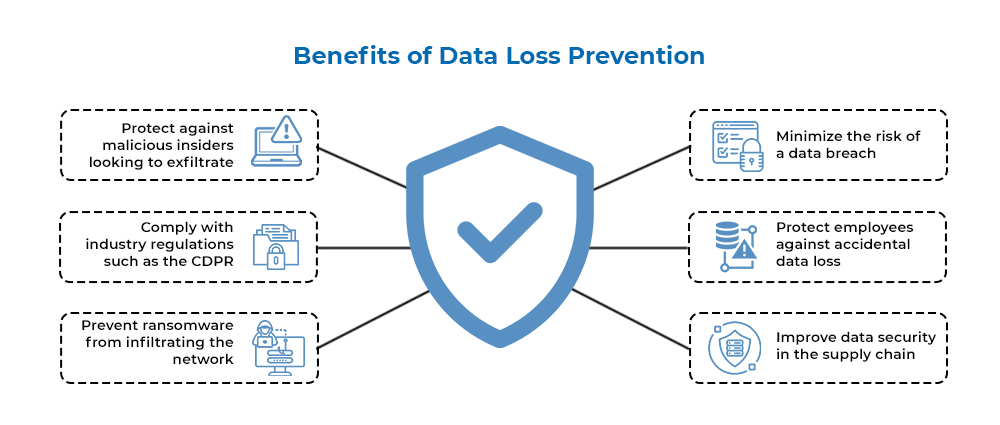
- Data protection: AWS offers a variety of data protection services, such as encryption, key management, and data loss prevention.
- Compliance: AWS offers a variety of compliance services, such as auditing, logging, and reporting.
In addition to these services, AWS also offers a number of security features that are built into the AWS platform. These features include physical security; infrastructure security; and operational security.
To ensure safety from cyber threats, both individuals and businesses can implement several key practices. Firstly, using strong passwords and regularly updating them is crucial to protect sensitive accounts and data. Secondly, being cautious about the information shared online helps prevent exposing personal or confidential details to potential hackers.
It’s essential to exercise caution when encountering emails or text messages from unknown senders, as these could be phishing attempts or malware-laden messages. Regularly updating software ensures that known vulnerabilities are patched, reducing the risk of exploitation by cybercriminals.
Employing a combination of firewall and antivirus software enhances the overall security posture, providing an added layer of defense against potential threats. Additionally, backing up data on a consistent basis safeguard against data loss in case of a breach or ransomware attack. By following these proactive measures, individuals and businesses can bolster their cyber defenses and minimize the chances of falling victim to cyber threats.
If you think that you have been the victim of a cyber-attack, there are a number of things you can do:
- Report the attack to the authorities.
- Change your passwords and security settings.
- Scan your computer for malware.
- Contact your bank or credit card company if your financial information has been compromised.
Conclusion
Given the whopping figures of cyber-related frauds in 2022, it’s not difficult to conclude that the escalating number of cyber threats in the UK poses a serious challenge. With a total value surpassing £2.3 billion and impacting over 2.7 million cases, it is clear that cyber security UK remains an essential priority to safeguard individuals, businesses, and critical infrastructure. The commendable efforts of the National Cyber Security Agency validate their commitment to countering these increasingly sophisticated attacks. Nevertheless, constant vigilance and proactive measures are crucial to effectively battle the devastating impact of cyber threats on all fronts.
TAGS
- Cyber Crime
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.