Latest Blogs

By AMSAT Dec 20, 2023
Unveiling the Hidden Advantages: Outsourcing SOC Services for Unrivaled Security
In today’s digitally-driven world, the threat of cyberattacks looms large. From ransomware and zero-day exploits to social engineering scams, businesses of all sizes are grappling with an inexplicably ominous threat of cyberattacks. Securing your organization’s sensitive data and critical infrastructure is not easy; it requires constant monitoring and a proactive approach. This is where the Security Operations Center (SOC) comes in.
An outsourced Security Operations Center acts as your organization’s cybersecurity control room, constantly screening your network for suspicious activity, examining threats, and coordinating incident response. But building and maintaining an in-house SOC can be a challenging endeavor, demanding considerable investment in infrastructure, human resource, and expertise. This is where the often-overlooked benefit of outsourcing SOC services emerges.
Outsourcing Cybersecurity
Envision a situation where you can exploit the capabilities of a dedicated team of cybersecurity experts, equipped with innovative technology and steeped in real-world experience, all without the burden of building and managing your own SOC infrastructure. Outsourcing SOC services unlocks this very scenario, providing your organization with instant access to a pool of cybersecurity experts, cutting-edge technology and infrastructure, and affordability and scalability.

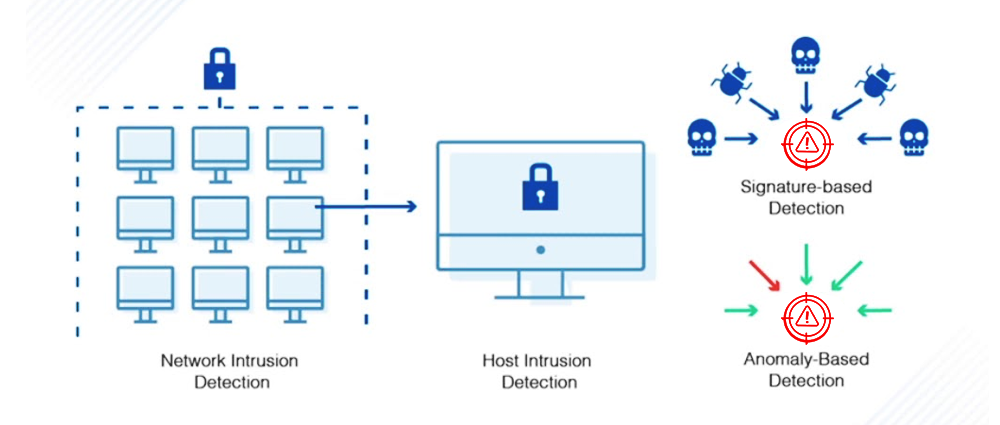
SOC Benefits
The advantages of outsourced SOC services extend far beyond simply having a team of experts watching your network. Here are some hidden benefits that can truly boost your organization’s security posture:
- Enhanced threat intelligence: SOC providers aggregate threat data from diverse sources, giving you access to a broader threat landscape and early warning of emerging vulnerabilities. This proactive approach allows you to adapt your security posture before threats strike.
- Continuous improvement: Leading SOC providers are constantly refining their processes and adopting new technologies, ensuring your security measures remain current and effective. You essentially benefit from their ongoing research and development, staying ahead of the ever-evolving cybercrime landscape.
- Improved incident response: When the inevitable attack occurs, having a seasoned SOC team by your side makes all the difference. Their expertise in containment, eradication, and recovery minimizes damage, mitigates downtime, and protects your reputation.
- Regulatory compliance: Outsourced SOC services can help you comply with industry regulations and data privacy laws by providing documented processes, audit trails, and reporting capabilities. This reduces the risk of hefty fines and reputational damage from non-compliance.
Choosing the Right Partner: Your Key to Success
Not all outsourced SOC services are created equal. While the advantages are undisputable, you must choose the right partner to maximize benefits. Here are some key factors to consider:
- Experience and expertise: Look for a provider with a proven track record of success in your industry and a team of certified cybersecurity professionals.
- Technology and infrastructure: Assess the provider’s security tools, platforms, and infrastructure to ensure they align with your needs and offer the necessary level of protection.
- Communication and transparency: Clear and consistent communication is vital. Choose a provider that prioritizes open communication and keeps you informed of any threats or incidents.
- Scalability and flexibility: Select a service that can adapt to your changing needs and security requirements as your business grows.
A Secure Future with Outsourced SOC
In today’s precarious digital world rife with all kinds of threats and challenges, organizations can no longer take their security for granted, or leave them to mere luck. By carefully choosing the right partner and exploiting the unseen benefits, you can ensure a future of unparalleled security for your organization, allowing you to focus on what matters most – your core business.
TAGS
- Security Operations Center
- Cyber Security
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.