Latest Blogs

By AMSAT Aug 17,2020
How to Manage Cybersecurity Risk and Compliance in Today's Challenging Environment
Introduction
In today’s fast-changing digital environment, businesses struggle with the fundamental significance of strong cybersecurity risk and compliance procedures. To protect sensitive data and guarantee regulatory conformance, a robust framework is required given the always changing cyber threat scenario.
Organizations must negotiate the complex landscape of changing laws, cutting-edge technology, and sophisticated assaults while facing rising difficulties. Cybersecurity risk and compliance management requires an integrated strategy that combines proactive threat assessment, diligent monitoring, and flexible policies. Businesses may strengthen their defenses and promote a safe digital ecosystem by embracing continuous learning, promoting cross-functional collaboration, and embracing cutting-edge technologies.
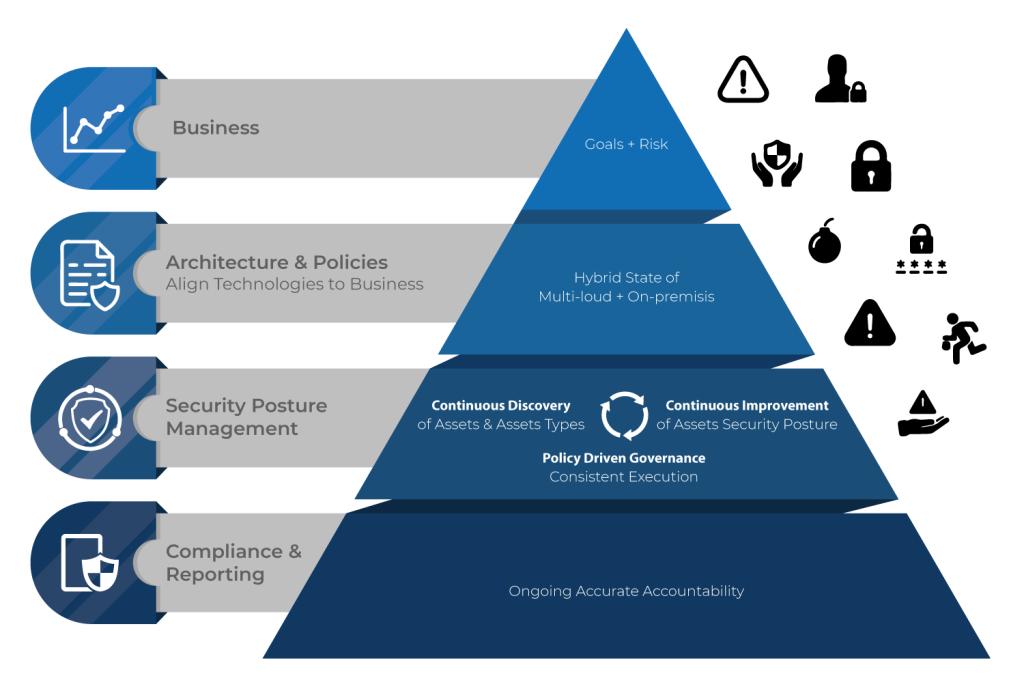
The Importance of Cybersecurity Risk and Compliance
Cybersecurity risk refers to the likelihood that a business will be attacked and the potential impact of such an attack. Compliance refers to the obligation of a business to follow certain rules and regulations.
Both cybersecurity risk and compliance are important for businesses because they can help to protect the business from financial loss, reputational damage, and legal liability.
The Challenges of Managing Cybersecurity Risk and Compliance in Today’s Environment
The challenges of managing cybersecurity risk and compliance in today’s environment are numerous. Here are a few of the most common challenges:
- The threat landscape is constantly evolving. New cyber threats are being developed all the time, which makes it difficult for businesses to stay ahead of the curve.
- The cost of cybersecurity is increasing. Businesses need to invest in a variety of security measures, such as firewalls, intrusion detection systems, and security awareness training.
- The human element is a major vulnerability. Employees can make mistakes that can lead to security breaches, such as clicking on malicious links or giving out their passwords.
- Regulatory compliance is becoming more complex. Businesses need to comply with a variety of regulations, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
Best Practices for Managing Cybersecurity Risk and Compliance
Despite the challenges, there are a number of best practices that businesses can follow to manage cybersecurity risk and compliance. Here are a few of the most important best practices:
- Create a comprehensive cybersecurity risk assessment. This assessment should identify the assets that need to be protected, the threats that those assets face, and the likelihood and impact of a successful attack.
- Implement a layered security approach. This approach uses a variety of security measures to protect the business, such as firewalls, intrusion detection systems, and security awareness training.
- Monitor and update security systems regularly. Security systems need to be monitored for vulnerabilities and updated with the latest security patches.
- Train employees on cybersecurity best practices. Employees need to be aware of the risks of cyberattacks and how to protect themselves and the business.
- Comply with applicable regulations. Businesses need to comply with all applicable regulations, such as the GDPR and the PCI DSS.
Conclusion
The urgent issues of cybersecurity and regulatory compliance cannot be ignored in today’s ever-changing business environment. Adopting the suggested best practices mentioned in this blog post will help organizations effectively defend themselves against cyberattacks while guaranteeing compliance with relevant laws.
Businesses can significantly improve their chances of success by engaging a skilled cybersecurity company that makes risk assessment simpler, making it easier to install effective security and allowing for continuing monitoring of vulnerabilities. By being informed on the most recent developments in cybersecurity, firms are better equipped to develop efficient mitigation plans and preventatively thwart new threats.
Investing in cybersecurity education gives workers the knowledge to understand the complexities of cyber threats, encouraging a watchful and secure work environment that protects both people and the company.
TAGS
- Cyber Crime
- Security Updates
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.


















