Latest Blogs

By AMSAT Dec 7, 2023
A Comprehensive Analysis of Intrusion Detection and Prevention Systems
Introduction
Are you an organization looking to secure critical data and infrastructure amidst today’s precarious business environment facing a looming threat of cyberattacks?
If yes, then you would be remiss not to deploy two key systems capable of detecting, analyzing, and responding to malicious activities: intrusion detection and prevention systems.
IDS vs IPS: Understanding the Difference
While often used interchangeably, IDS and IPS are distinct security solutions that serve complementary purposes. IDS chiefly focuses on monitoring and analyzing network traffic, system logs, and user activity to identify suspicious or malicious behavior. It acts as a sentinel, alerting security personnel to potential threats before they can wreak havoc.
IPS, on the other hand, takes a more proactive approach, actively intercepting and blocking malicious traffic before it can reach its intended target. It acts as a gatekeeper, preventing intrusions from breaching the network’s defenses.
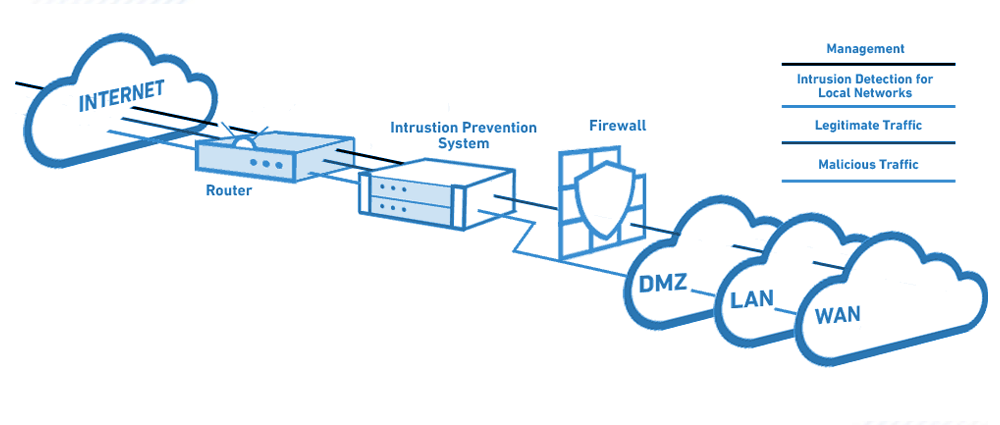
IDS/IPS Logs: Generating Valuable Data
IDS and IPS generate a wealth of valuable data in the form of logs, capturing details of network activity, system events, and detected intrusions. These logs serve as a crucial resource for security teams, providing insights into the evolving threat landscape and enabling them to refine their security strategies.
Analyzing IDS/IPS logs allows security analysts to:
- Detect patterns and trends in malicious activity
- Track attacker behavior and methods
- Prioritize security responses based on the severity of threats
- Gauge the effectiveness of existing security measures
Differences between IDS and IPS
While Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are both security tools that help protect networks from malevolent attacks, they differ in the way they function.
IDS is a passive system that monitors network traffic for suspicious activity. It does not take any action to stop an attack, but it can generate alerts that notify security personnel of a potential threat, allowing them to examine and take corrective action before the attack can cause damage.
IPS is an active system that can take steps to block or stop an attack in progress. It can do this by dropping malicious packets, resetting connections, or even shutting down systems. IPS systems are typically deployed alongside IDS systems to provide a more comprehensive level of security.
Can IDS and IPS Work Together?
Yes, they can. When deployed together, IDS and IPS form a powerful security duo. IDS provides real-time visibility into network activity, while IPS takes immediate action to thwart threats. This synergy offers complete protection against an extensive range of cyber threats.
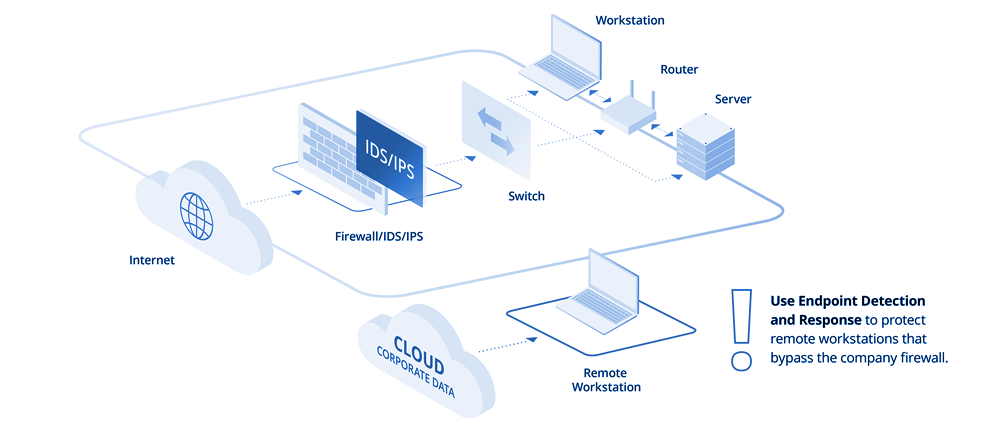
IDS and IPS: The Keystones of Network Security
IDS and IPS have become essential components of modern cybersecurity architectures, offering organizations a critical line of defense against the ever-rising sophistication of cyberattacks. By effectively detecting and preventing intrusions, IDS and IPS help secure valuable data, maintain network integrity, and defend organizations from reputational damage.
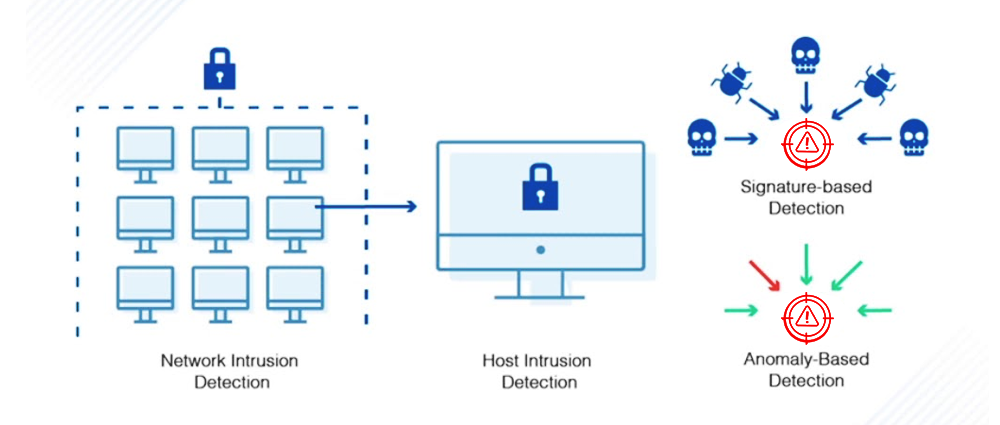
AMSAT—Your Reliable Partner in Cybersecurity
Given the precarious business landscape plagued by threat actors hell-bent on causing damage to large and medium enterprises, cybersecurity has become a necessity, a fact that entrepreneurs have finally come to realize. AMSAT, a top cybersecurity service provider, offers comprehensive IDS solutions to help organizations fortify their defenses against cyber threats.
Our expert team can help you select and deploy the right IDS solution for your organization’s needs, while configuring and managing your IDS systems effectively. We are also adept at analyzing IDS logs to identify and respond to threats swiftly.

AMSAT’s commitment to excellence and innovation in cybersecurity ensures that your organization remains protected against the latest threats.
Conclusion
Intrusion detection and prevention systems (IDS/IPS) are indispensable tools for organizations seeking to secure their networks and data from the ever-evolving threat landscape. By understanding the distinction between IDS and IPS, taking advantage of the power of IDS/IPS logs, and making the most of the expertise of reliable cybersecurity providers, organizations can effectively identify, prevent, and respond to cyber threats, ensuring the security and integrity of their critical assets.
TAGS
- Cyber Security
- IDS
- IPS
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.









