Latest Blogs
By AMSAT Sep 19,2023
Types of Endpoint Application Isolation and Containment Technology
In today’s digital world, securing endpoints such as computers, mobile devices, and servers has become increasingly important.
Organizations around the world consider endpoint security to be a major challenge, with application isolation and containment technology being one key feature of this aspect. This technology plays a critical role in preventing malware, data breaches, and unauthorized access to sensitive information.
Containment applications, which is another primary aspect of this technology, play a critical role in isolating and neutralizing threats before they can spread to other parts of a network. This blog will delve into various types of endpoint application isolation and containment technology and how they can enhance security.
1. Sandboxing Technology
Sandboxing is a security method that isolates applications in a controlled environment to prevent them from spreading malware to the rest of the system. Sandboxes limit applications’ access to system resources and data, providing a safe space for them to execute.
Sandboxing is particularly effective against zero-day exploits, which are attacks that exploit vulnerabilities in software that the software vendor is not aware of. When a suspicious file or application is opened in a sandbox, its behavior is carefully supervised. If any malicious activity is spotted, the sandbox can terminate the application, preventing it from damaging the host system.
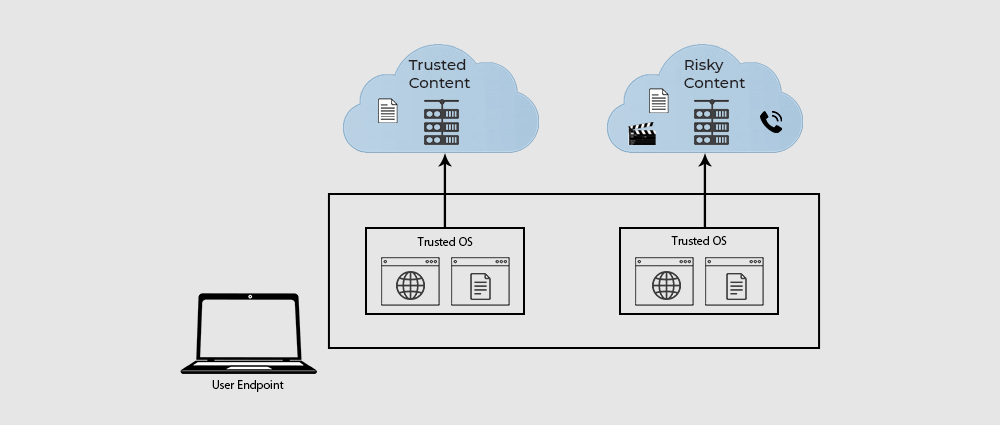
2. Virtualization-Based Isolation
A security technique that isolates applications in separate virtual machines (VMs) or containers, virtualization-based isolation provides a higher level of security than traditional sandboxing. It prevents malware from escaping one container and contaminating others or the host system.
Each virtual machine or container is a separate environment with its own resources and operating system. This prevents programs running in several VMs or containers from interacting with one another or the host system. Even if one application is infected, this isolation stops malware from spreading to other applications.
Enterprise environments frequently use virtualization-based isolation to separate sensitive workloads and applications. For instance, a business might use virtualization-based isolation to isolate its financial systems from its customer relationship management (CRM) apps by running each in a different virtual machine (VM) or container. This helps prevent malware that might attack CRM software from compromising the banking applications.
3. Containerization
A technique of isolating applications in lightweight containers that share the host operating system’s kernel, containerization makes containers more efficient than virtual machines (VMs). Containers also have their own file systems, libraries, and resources, which further isolates them from each other and the host system.
Because containerization enables quicker and more effective application deployment and scalability, it is a common strategy in DevOps and microservices contexts. Since containers may be easily moved between several cloud providers, they are also ideally suited for cloud computing.
To maintain security, it’s crucial to configure containers properly. Containers are vulnerable to some attacks because they share the same kernel as the host system. For instance, the entire host system might be compromised if a malicious container is successful in exploiting a kernel vulnerability.
4. Application Sandboxing on Mobile Devices
On mobile devices, application sandboxing is a security technique that isolates each app in its own environment, limiting its access to device resources. This prevents malicious apps from accessing sensitive user data or interfering with the core functionality of the operating system.
Mobile operating systems like iOS and Android use sandboxing to protect users from malware and other security threats. Sandboxing is also used to prevent apps from crashing or interfering with each other.
In addition to sandboxing, mobile operating systems also use permission systems to control how apps access device resources. When an app requests access to a resource, such as the camera or location services, the user is prompted to approve or deny the request. This gives users control over their privacy and security.

5. Network-Based Isolation
A security approach that isolates applications or devices on separate network segments, network-based isolation is different from endpoint isolation, which separates applications on individual devices.
Network-based isolation is commonly used in enterprise settings to protect critical systems and sensitive data. By isolating these resources on a separate network segment, security cab be better maintained sue to limited potential impact of a breach.
Conclusion
Endpoint application isolation and containment technology is a crucial component of contemporary cybersecurity methods. Sandboxing, virtualization-based isolation, containerization, mobile app sandboxing, and network-based isolation are some of the technologies that can help secure against a variety of risks, from malware to unauthorized access.
While each technology has its own strengths and weaknesses, a layered approach that combines multiple techniques can provide strong security for endpoints. Amid an ever-evolving digital landscape, keeping abreast of these technologies and employing best practices is key to protecting sensitive data and systems.
TAGS
- Endpoint Security
- Containment Technology
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.










owpnswoww says:
Types of Endpoint Application Isolation and Containment Technology – Amsat
aowpnswoww
owpnswoww http://www.g6178yy8125s8baaq5me0pt4l44t75mws.org/
[url=http://www.g6178yy8125s8baaq5me0pt4l44t75mws.org/]uowpnswoww[/url]