Latest Blogs

By AMSAT Nov 24, 2023
The Future of Cybersecurity: Top Trends to Watch in 2024
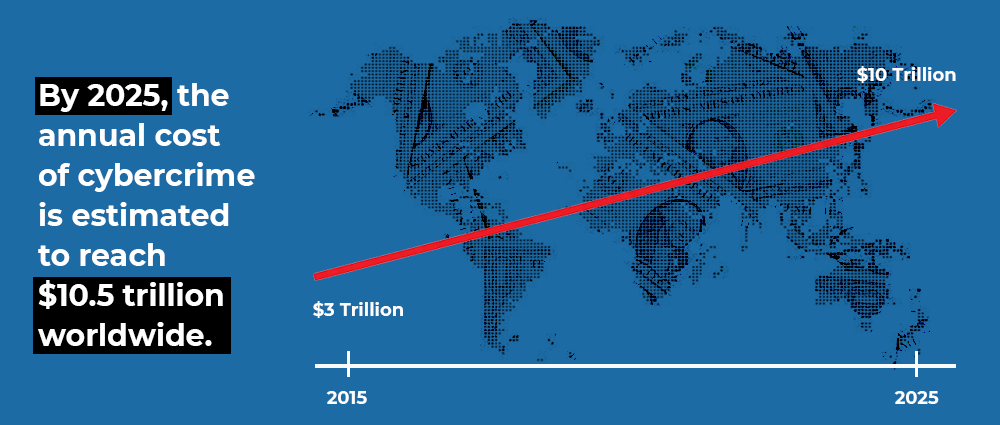
Cybersecurity is a new and potent threat facing the organizations in the modern world. While the current cybersecurity landscape faces countless threats from cybercriminals, all bets are off when it comes to the trends in cybersecurity in 2024 and beyond.
In 2023, we saw a number of new trends emerge, and in 2024, we can expect to see even more. This blog post will discuss the top cybersecurity trends to watch in 2024.
Top Cybersecurity Trends to Watch in 2024
1. Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are already being used extensively in cybersecurity. In 2024, we can expect to see even more organizations adopt AI and ML solutions to detect and prevent cyberattacks. AI and ML can be used to analyze large amounts of data to identify patterns and anomalies that may indicate a cyberattack. They can also be used to automate tasks such as threat detection and incident response.
2. High demand for professionals with cybersecurity skills
This will be one of the top cybersecurity trends in 2014 and beyond, given an acute scarcity of professionals capable of protecting organizations and financial institutions against a variety of cyberattacks. As 2023 comes to a close, we are expected to see new job postings for cybersecurity experts for the new year, as business owners are spending sleepless nights finding out ways to grapple with the looming threat of cyberattacks.
3. Zero Trust
Zero trust is a security model that assumes that no user or device should be trusted by default. This model requires all users and devices to be verified before they are granted access to resources. Zero trust is becoming increasingly popular as organizations seek to improve their security posture and protect their data from unauthorized access.
4. Data Privacy Regulations
Privacy trends in 2023 witnessed a sharp rise, and we saw the implementation of the General Data Protection Regulation (GDPR) in the European Union. However, the situation is likely to turbocharge in the years ahead: In 2024, we can expect to see more data protection trends emerge, bringing a seismic shift in the realm of cybersecurity.
5. Biometric Authentication
Biometric authentication is becoming increasingly common as a way to verify users’ identities. In 2024, we can expect to see more organizations adopt biometric authentication solutions, such as fingerprint and facial recognition.

6. Supply Chain Risks
Supply chain risk management is fast becoming a top priority, as companies lose millions of dollars due to supply disruption, cost volatility, non-compliance fines and incidents that hurt both their brand value and reputation. In 2024, organizations will need to be more aware of the risks associated with their supply chains and take steps to mitigate those risks.
7. Cyber Warfare
Typically defined as a cyber-attack or series of attacks that target a country, cyber warfare can wreak havoc to government and civilian infrastructure, resulting in significant damage to the state and even loss of life. In 2024, we can expect to see more cyberattacks from nation-states. Organizations will need to be prepared to defend themselves against these attacks.
8. Automation and Integration
Given the size of data which is constantly on the increase, it is evident that automation and integration will lie at the heart of the cybersecurity domain in 2024. The hectic, fast-paced work will also exert remarkable pressure on professionals to deliver quick and proficient solutions, making automation an integral feature of cybersecurity.
9. Next-Level Phishing Attacks
2024 is likely to see an escalation in the sophistication of social engineering attacks, which trick users into granting unauthorized access to systems. Since using generative artificial intelligence (AI) tools, such as OpenAI’s ChatGPT, allows a large number of hackers to employ more sophisticated and personalized strategies in their attacks, the incidence of deepfake attacks is projected to rise in the future.
10. 5G Networks
In 2024 and beyond, the rollout of 5G networks will improve security as well as revolutionizing connectivity. Data transmission security will be largely dependent on improved encryption and low-latency communication, even in the busiest and most dynamic contexts.
Preparing for the Future of Cybersecurity
In order to prepare for the future of cybersecurity, organizations need to take a number of steps. First, they need to assess their current cybersecurity posture and identify any risks. Second, they need to develop a cybersecurity strategy that addresses those risks. Third, they need to implement appropriate security controls. Fourth, they need to train their employees on cybersecurity awareness. Fifth, they need to continuously monitor their networks for signs of cyberattacks.
By taking these steps, organizations can help to protect themselves from the evolving cybersecurity threat landscape.
Conclusion
While it’s difficult to say definitively about the future of cybersecurity and its long-term implications on the overall technology landscape, organizations need to be more cautious and watchful about how they should protect themselves from the mischievous designs of vicious actors. But the one thing that ensures enterprises’ safety and security is their ability to be aware of the latest trends and take proactive measures to protect their data.
TAGS
- Cyber Security
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.