Latest Blogs

By AMSAT August 31st, 2025
What is the Difference Between Phishing and Spear Phishing
If you’ve ever received a weird email about a password reset you didn’t request, a delivery you never ordered, or an invoice you don’t recognize, you’ve met phishing. Think of phishing as a mass-produced scam: attackers send the same bait to thousands or millions of people, hoping some will click.
Spear phishing is different. It’s not a wide net; it’s a harpoon. Attackers carefully research a specific person (or small group) and tailor the message to look incredibly real, often referencing your boss’s name, your project, or your company tools. Same goal (steal data, money, or access), but far more personal and targeted.
In short:

- Phishing = bulk, generic, automated
- Spear phishing = targeted, personalized, research-driven
What Does a Phishing Email Look Like? (Phishing Examples)
Classic phishing examples often include:- “Your account will be locked, verify now” with a link to a fake login page.
- A fake shipping notice (UPS, DHL, FedEx) with a “track your package” button.
- A streaming service “payment failed” alert asking for updated card details.
- A bank “unusual activity” notice with a link to “secure your account.”
What Does a Spear Phishing Email Look Like? (Spear Phishing Examples)
Spear phishing examples are more convincing because the sender knows something about you:- An email that appears to be from your CFO, referencing your team’s current vendor, asking you to pay an attached invoice by EOD.
- A message that looks like it’s from IT, mentioning the exact tool you use (e.g., Microsoft 365, Slack, Notion), asking you to “re-authenticate” via a link.
- A recruiter referencing your recent conference talk and asking you to open a “role description” (malicious attachment).
What Is Whaling?
Whaling is spear phishing aimed at high-value targets, executives, founders, finance leaders, or anyone who can authorize payments and access sensitive systems. Because these people are busy and often travel, attackers lean on urgency: “Please approve this vendor payment before my flight.” Whaling emails may be short and informal (just like real executive emails), and attackers often instruct recipients to bypass normal processes “just this once.”The Types of Phishing Attacks (Quick Tour)
When people ask about the types of phishing attacks, they usually mean delivery channels and techniques. The big four:- Email phishing: The classic. Spoofed sender, fake login pages, malicious attachments.
- Spear phishing / Whaling: Highly targeted email scams (see above).
- Smishing: Phishing via SMS (“Your parcel is pending, pay customs fees here”).
- Vishing: Voice phishing via phone calls or voicemails (often pretending to be your bank, IT, or government).
Why Spear Phishing Works So Well
Spear phishing succeeds because it looks like normal work:- It references real people and projects.
- It lands at the right time (e.g., during an active vendor switch or quarter-end crunch).
- It asks for something plausible (invoice payment, document review, MFA reset).
- It often uses legitimate tools (e.g., a real cloud storage link hosting malware or a simple OAuth consent request).
Two Data Points That Show the Scale
In 2024, the FBI’s Internet Crime Complaint Center recorded 859,532 complaints of suspected internet crime and over $16 billion in reported losses, a 33% jump from 2023. Source: FBI press release (April 23, 2025). Within that, phishing/spoofing alone accounted for 193,407 complaints in 2024. Source: FBI IC3 2024 Annual Report (pages 17–18).How to Spot the Difference Between Phishing and Spear Phishing (At a Glance)
The difference between phishing and spear phishing boils down to scope and specificity:
Practical Defenses That Actually Work
1) Security Awareness Training (make it real, keep it short)
Quarterly bite-sized sessions + monthly phishing simulations are far more effective than an annual 60-minute lecture. Focus on:- Hover-to-inspect links, or long-press on mobile.
- Verify sender domain and reply-to.
- Slow down on urgent or unusual requests.
- Use secondary channels to confirm (e.g., call your CFO, ping your boss on Slack).
- How to report phishing email quickly (see below).
2) Email Security Solutions (your first filter)
Modern email security solutions do more than spam blocking. Look for features such as:- URL rewriting & time-of-click scanning (malicious links that “arm” later are caught).
- Attachment sandboxing (detonates suspicious files safely).
- Impersonation and brand-spoof detection (flags look-alike senders and domains).
- Authentication enforcement (DMARC, DKIM, SPF) to reduce spoofing.
- User-reported phishing integration (turn reports into block rules fast).
3) Best Anti-Phishing Software (what “best” looks like)
There is no single “best,” but the best anti-phishing software stack typically includes:- Secure email gateway or cloud email security that layers on top of Microsoft 365/Google Workspace.
- Advanced threat protection (sandboxing, behavioral analysis).
- Account takeover & OAuth consent monitoring for cloud apps.
- Domain protection (look-alike domain monitoring, DMARC enforcement).
- Automated remediation (pull malicious emails from inboxes after delivery).
4) Strong Identity & Access Controls (assume compromise)
Even if someone clicks, you can still limit damage:- MFA everywhere, especially for email, VPN, and admin tools.
- Conditional access (block risky logins by geography, device posture, impossible travel).
- Least-privilege access, don’t give finance rights to everyone.
- Password managers (unique, strong credentials; they also flag fake domains).
- Device hardening (EDR, automatic patching, disk encryption).
5) How to Stop Phishing Emails (reduce the noise)
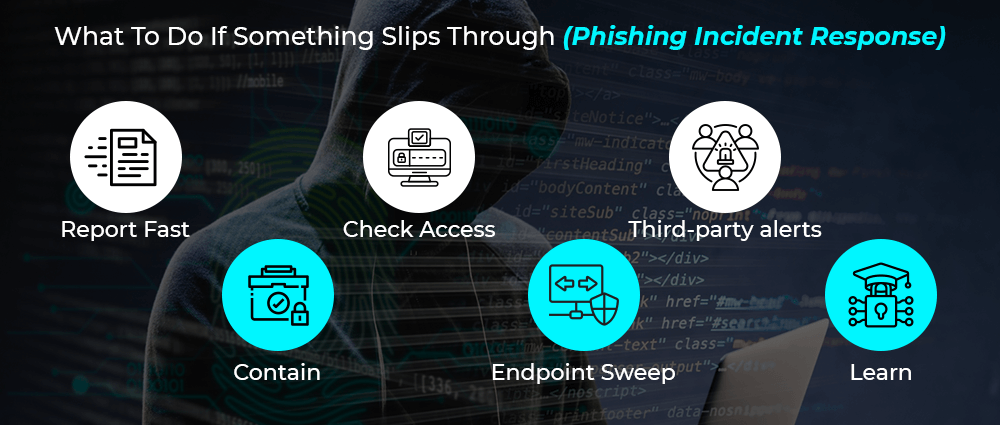
To reduce the noise and stop phishing emails, organizations should enforce DMARC with a “reject” policy once traffic is monitored and aligned. Blocking newly registered or risky domains and throttling links from consumer URL shorteners adds another layer of safety. Inline banners can also help by flagging external senders or sensitive terms such as “wire transfer,” “gift cards,” or “W-2s.” It’s equally important to regularly purge look-alike domains from allowlists and keep mailing lists or group addresses off public websites, or at least obfuscate them to make harvesting harder.What To Do If Something Slips Through (Phishing Incident Response)
Despite solid defenses, one crafty message can still get through. Your phishing incident response playbook should be muscle memory:
-
Report Fast
-
Contain
-
Check Access
-
Endpoint Sweep
-
Third-party alerts
-
Learn
Phishing vs Spear Phishing: A Quick Checklist for Employees
When a suspicious message lands, ask:- Is the request expected? If not, slow down.
- Do I recognize the sender domain? Check for subtle misspellings (yourc0mpany.com).
- Is there urgency or secrecy? (“Please don’t loop anyone else in.”)
- Does the link match the real site? Hover/long-press to preview.
- Is the attachment necessary? If unsure, confirm via a different channel.
- Am I being asked to break process? Payments, W-2s, and gift cards are red flags.
Bringing It All Together
Phishing is “casting a wide net,” while spear phishing is “hand-crafted bait for a specific target.” Both are social engineering techniques designed to exploit human attention and trust. The best defense is a layered approach; people (through security awareness training), technology (email security solutions and the best anti-phishing software), and process (a fast phishing incident response plan). Make reporting simple, and reward employees who flag suspicious messages, even if they turn out to be harmless. This culture of vigilance strengthens your human firewall. At Amsat, we help organizations achieve exactly that by combining advanced cybersecurity solutions with tailored awareness programs, robust email security, and 24/7 incident response support, so you can stay ahead of evolving phishing threats.Frequently Asked Questions
What is the most famous example of phishing?
One of the most cited early examples is the PayPal phishing wave in the early 2000s, attackers emailed fake “account verification” notices that led to look-alike login pages and harvested credentials. In the corporate world, many point to high-profile Business Email Compromise scams where companies were tricked into wiring millions to attacker-controlled accounts (sometimes via look-alike vendor domains). These cases highlight how convincing social engineering can be and why verification via a second channel is crucial.What are the four types of phishing?
A simple way to categorize the types of phishing attacks is:- Email phishing (mass, generic messages)
- Spear phishing/whaling (targeted, executive-focused variants)
- Smishing (SMS/text)
- Vishing (voice/phone)
TAGS
- Cyber Threats
- Cyber Security
- SOC
- Managed SOC
Recent Blogs
afnan ali
Dec 31 2025
-
Category:
afnan ali
Sep 30 2025
-
Category:
afnan ali
Aug 31 2025
-
Category:
Ali hammad
Jul 31 2025
-
Category:
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.