By AMSAT November 27, 2025
Threat and Vulnerability Management: 101 Cybersecurity Guide
Cybersecurity is no longer just an IT issue. It is a business survival issue. Every organization today relies on digital systems, cloud platforms, applications, and networks. This dependency also creates opportunities for cybercriminals. A single overlooked weakness can lead to data breaches, downtime, financial losses, and reputational damage.
This is where Threat and Vulnerability Management becomes critical. It helps organizations identify weaknesses before attackers do, understand real threats, and reduce risk in a structured and measurable way.
Today, we will break down everything you need to know about Threat and Vulnerability Management in plain language. You will learn what it is, why it matters, how to build a vulnerability management program from scratch, and which best practices help organizations stay secure in the long run.
What Is Threat and Vulnerability Management?
Threat and Vulnerability Management is a continuous cybersecurity process that focuses on identifying threats, discovering vulnerabilities, assessing risk, and reducing the chances of a successful cyberattack.
It combines two essential security disciplines. Threat management focuses on attackers and malicious activities. Vulnerability management focuses on weaknesses in systems, software, and configurations. When used together, they form a proactive defense strategy rather than a reactive one.
Defining Vulnerability Management in Cybersecurity
The first things we should be asking and learning about are:
What is Vulnerability Management in Cybersecurity?
Vulnerability management in cybersecurity is the structured process of finding, evaluating, prioritizing, and fixing security weaknesses across an organization’s IT environment. These weaknesses may exist in operating systems, applications, cloud workloads, networks, databases, or even user access controls. The goal is not just to detect vulnerabilities but to reduce the risk they pose to business operations.
Common Types of Cybersecurity Vulnerabilities
Some of the common vulnerabilities can include:
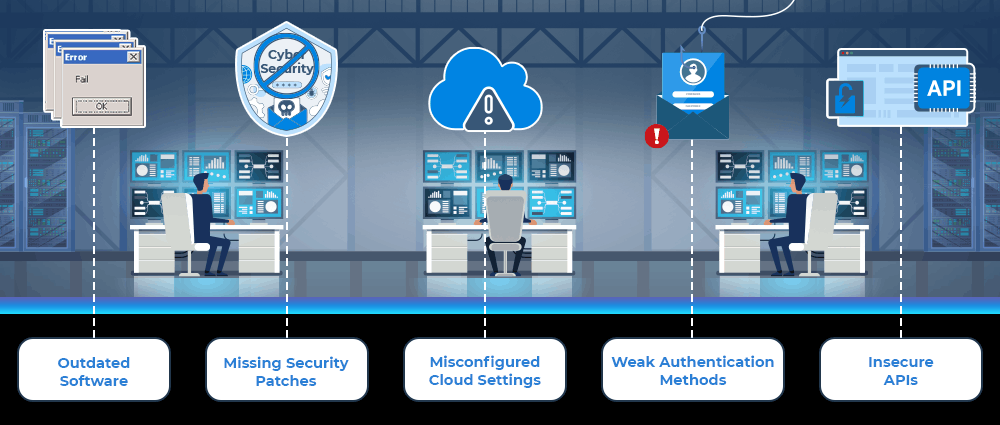
A robust vulnerability management program ensures these issues are continuously monitored and addressed.
Why Vulnerability Management Is an Ongoing Process?
New vulnerabilities are discovered daily. Systems change, updates are deployed, and new applications are added. This makes vulnerability management a continuous cycle rather than a one-time activity.
What is a Vulnerability Management Program?
A vulnerability management program is a formal and documented approach that defines how an organization identifies, tracks, prioritizes, remediates, and reports vulnerabilities. It includes people, processes, tools, and governance.
What is a vulnerability management program in practice?
In practice, it means having scheduled scans, defined remediation timelines, clear ownership, reporting metrics, and management oversight. Without a program, vulnerability management becomes ad hoc and ineffective.
Connection to patching
A vulnerability and patch management program ensures that vulnerabilities are not only discovered but also fixed using patches, configuration changes, or compensating controls.
The Critical Need for Threat and Vulnerability Management
Cyberattacks are becoming more frequent, more automated, and more targeted. Organizations that rely only on traditional security tools often discover threats too late.
Why Modern Enterprises Require a Proactive Defense?
Increasing Attack Frequency
Cyber incidents continue to rise globally. Studies show that 66 percent of organizations reported an increase in cybersecurity incidents in recent years.
This highlights how reactive security approaches are no longer enough.
Exploitable Weaknesses Everywhere
Research also shows that 67 percent of organizations had at least one critical vulnerability that could be exploited by attackers.
These weaknesses often remain unpatched due to a lack of visibility or prioritization.
Business Impact of Breaches
Cyberattacks can disrupt operations, expose customer data, erode brand trust, and result in regulatory penalties.
Proactive Threat and Vulnerability Management helps reduce these risks before damage occurs.
The Role of Risk Elimination in Cybersecurity
Understanding risk elimination
Risk elimination means reducing the likelihood that a vulnerability will be exploited and minimizing its impact if it is. This does not mean eliminating all risk, which is impossible, but managing it intelligently.
Prioritization over volume
Most organizations face thousands of vulnerabilities. A cyber vulnerability management program focuses on the vulnerabilities that matter most rather than trying to fix everything at once. This enables major risks to be catered first and protects the organization from larger losses.
Threat Management vs. Vulnerability Management: Key Differences
Although closely related, threat management and vulnerability management serve different purposes within cybersecurity.
| Aspect | Threat Management | Vulnerability Management |
| Definition | Focuses on identifying and mitigating potential cyber attacks or malicious activities. | Focuses on discovering, assessing, and fixing weaknesses in systems, applications, or networks. |
| Primary Goal | Prevent attacks and reduce exposure to threats. | Reduce the likelihood of vulnerabilities being exploited. |
| Question Answered | “What could attack us?” | “What weaknesses do we have that could be exploited?” |
| Scope | Broader view: external and internal threats, including malware, phishing, ransomware, and hacking attempts. | Narrower view: system flaws, misconfigurations, outdated software, and missing patches. |
| Tools Used | Threat intelligence platforms, security monitoring tools, and intrusion detection systems. | Vulnerability scanners, patch management tools, and configuration assessment tools. |
| Process | Continuous monitoring for threat activity, analyzing attack patterns, and responding to incidents. | Regular scanning, prioritizing vulnerabilities, applying patches, and tracking remediation. |
| Outcome | Awareness of potential attacks and readiness to respond. | Systems hardened against exploitation, fewer security gaps. |
Why Are Both Threat Management and Vulnerability Management Required Together?
Threat management focuses on identifying malicious actors, attack techniques, malware, phishing campaigns, and suspicious activities. It answers the question of who is trying to attack us and how.
Whereas vulnerability management focuses on weaknesses inside systems that attackers could exploit. It answers the question of where an attacker could get in.
Threats often target specific vulnerabilities. Without vulnerability management, threat detection alone cannot prevent attacks. Without threat intelligence, vulnerability data lacks context.
Comparing Threat and Vulnerability Management by Risk Elimination
Threat Management Approach
Threat management reduces risk by detecting and stopping attacks in progress using monitoring, alerts, and response mechanisms.
Vulnerability Management Approach
Vulnerability management reduces risk by eliminating weaknesses before they are exploited. Together, they reduce both the attack surface and the success rate of cyberattacks.
The Lifecycle of a Cyber Vulnerability Management Program
Threat and Vulnerability Management follows a structured lifecycle that repeats continuously. A cyber vulnerability management program is most effective when it follows a structured lifecycle. This ensures that vulnerabilities are not only found but also continuously monitored, assessed, and remediated. Think of it as a cycle that repeats to keep your systems secure.
1. Asset Discovery
The first step is to know what you have. Identify all hardware, software, cloud services, and devices in your organization.
Maintaining an up-to-date inventory helps ensure that no system or application is left unprotected. For example, servers, laptops, network devices, and critical business applications are all included.
2. Vulnerability Identification
Scan all assets for known weaknesses or vulnerabilities:
- Use automated vulnerability scanners, threat intelligence feeds, and manual testing when needed.
- This step helps uncover outdated software, missing patches, misconfigurations, and other security gaps.
Example: A web application running an old version of software that is prone to attack is detected.
3. Risk Assessment
After identifying vulnerabilities, determine how risky each one is, like:
- Consider factors like the severity of the vulnerability, the likelihood of it being exploited, and the potential impact on the organization.
- Assign a priority to each vulnerability so that the most critical ones are addressed first.
For example, a critical vulnerability on a public-facing server is prioritized over a minor vulnerability on an internal printer.
4. Remediation and Mitigation
- Fix vulnerabilities based on their priority.
- Remediation might include applying patches, changing configurations, or upgrading software.
- Mitigation strategies can be used when immediate fixes are not possible, such as adding network firewalls or restricting access.
- Example: Applying a patch to a critical server immediately after a vulnerability is discovered.
5. Verification and Validation
- Post remediation, the first step is to check to what extent the vulnerabilities have been taken care of.
- By conducting follow-up scans, one can be sure that there was no flaw or defect in the patch or fix applied.
- With this step, it is guaranteed that no loopholes remain unaddressed or wrongly addressed at all.
An illustration: The scanner signifies that a vulnerability detected earlier is not there any longer.
6. Continuous Monitoring
- The adaptation of threats through the cyber sphere is a continuous process, which makes new ones appear over time or existing ones to reappear.
- Thus, the operation of continuous monitoring of networks, systems, and applications will be able to discover new vulnerabilities as well as old ones.
In addition, updating of threat intelligence feeds and scanning frequency will be done periodically in order to be in line with the changes.
7. Reporting and Improvement
- Make a comprehensive record of vulnerabilities, remediation measures, and the effectiveness of the program.
- Create reports for IT personnel, management, and the audit department.
Factoring insights from previous incidents and scans into the process to enhance it while at the same time reducing future risks.
Example: Reporting that shows patching times have decreased over the last quarter indicates the program is improving.
The lifecycle of a cyber vulnerability management program is a continuous loop: discover assets, identify vulnerabilities, assess risk, remediate, verify fixes, monitor, and improve. By following this cycle, organizations can proactively reduce risks, prevent attacks, and maintain a strong cybersecurity posture.
Core Components of a Threat and Vulnerability Management Program
A successful program includes multiple interconnected components that work together.
Asset Discovery and Inventory Management
Why asset visibility matters? Asset discovery ensures every system, device, application, and cloud workload is accounted for.
Dynamic Environments: Modern IT environments change frequently. Automated discovery ensures visibility remains accurate.
Vulnerability Scanning and Assessment Tools
Automated Scanning: Tools scan systems for known vulnerabilities using databases of known security flaws.
Contextual Analysis: Advanced tools consider asset importance, exposure, and threat intelligence.
The Integration of a Vulnerability and Patch Management Program
Closing the loop: Scanning without patching creates visibility without protection. Integration ensures vulnerabilities are fixed.
Patch prioritization: Critical patches are deployed first to reduce time-to-exploit.
How to Build a Vulnerability Management Program from Scratch
Step 1: Define Objectives
Before starting, you need to know exactly what your vulnerability management program is trying to achieve.
- Decide whether the focus is on reducing data breaches, improving system security, meeting regulatory compliance, or all of these.
- Setting clear goals ensures your team knows what success looks like and helps prioritize actions.
- Example: “Our goal is to patch all critical vulnerabilities within 30 days of discovery.”
Step 2: Assess Current Security Posture
Understanding your current security state is crucial before you make improvements.
- Conduct an inventory of all your systems, software, devices, and applications.
- Identify existing vulnerabilities such as outdated software, misconfigured settings, or weak passwords.
- Check past incidents and known threats to see where your organization has been exposed before.
- This step gives you a clear picture of what needs attention first.
Step 3: Choose Tools and Technologies
Having the right tools makes the program efficient and effective.
- Vulnerability Scanners: Automatically scan systems for weaknesses.
- Patch Management Solutions: Help deploy updates quickly across multiple systems.
- Threat Intelligence Platforms: Provide information about new threats and vulnerabilities.
Choose tools that fit your organization’s size, infrastructure, and complexity.
Step 4: Implement Processes
Define step-by-step processes for handling vulnerabilities so nothing is missed.
- Determine how often scans should run.
- Decide how to assess the severity of vulnerabilities and assign risk scores.
- Create a method to prioritize which vulnerabilities need urgent attention.
- Outline how remediation will be done, such as applying patches, updating configurations, or other fixes.
Having documented processes ensures consistency and accountability.
Step 5: Assign Responsibilities
Clear ownership is essential for an effective program.
- Assign specific roles to IT teams, security teams, and management.
- Example: IT team applies patches, security team monitors threats, and management reviews reports.
- Responsibilities should be clearly documented so everyone knows their tasks.
Step 6: Train Employees
Humans are often the weakest link in cybersecurity, so education is key.
- Provide staff with basic cybersecurity training, including phishing awareness, password security, and safe internet practices.
- Train teams involved in vulnerability management on using the tools and following the processes.
- Regular training helps prevent mistakes that could expose the organization to threats.
Step 7: Monitor and Improve
A vulnerability management program is not a one-time project; it needs continuous attention.
- Regularly review metrics like the number of vulnerabilities found, time to patch, and risk reduction.
- Monitor systems for new vulnerabilities and emerging threats.
- Use lessons learned from incidents to improve processes.
Continuous improvement ensures your program stays effective as threats evolve.
Threat and Vulnerability Management Program Best Practices
Best practices help ensure long-term success and continuous improvement. These are some of the best practices being used in vulnerability management programs that you can try in yours and prepare correctly for the future:
Regular Scanning
Regular scanning helps organizations discover new vulnerabilities as soon as they appear.
By scanning systems frequently, teams can identify outdated software, missing patches, and security gaps before attackers exploit them.
Risk-Based Prioritization
Not all vulnerabilities are equally dangerous, so focusing on the most critical ones is essential. Risk-based prioritization ensures that vulnerabilities with the highest business and security impact are addressed first.
Patch Promptly
Applying patches quickly reduces the time attackers have to exploit known vulnerabilities. A clear and timely patching process helps keep systems secure and up to date.
Continuous Monitoring
Continuous monitoring allows organizations to detect new threats and vulnerabilities in real time.
This ongoing visibility helps security teams respond faster and stay ahead of evolving cyber risks.
Documentation
Proper documentation keeps track of identified vulnerabilities, fixes, and improvements over time. Clear records support audits, compliance needs, and help measure the success of the vulnerability management program.
Collaboration
Collaboration between IT teams, security teams, and management ensures vulnerabilities are handled efficiently.
When everyone understands their role, security gaps are resolved faster and more effectively.
Conclusion
Threat and Vulnerability Management is not optional in today’s digital world. It is a foundational cybersecurity capability that protects organizations from known weaknesses and emerging threats. By implementing a structured vulnerability management program, aligning threat intelligence, and following best practices, organizations can significantly reduce cyber risk and build long-term resilience.
This is where Amsat can help businesses move from strategy to action. Amsat supports organizations in building and managing effective threat and vulnerability management programs, from identifying critical assets and vulnerabilities to prioritizing risks and ensuring timely remediation.
With a practical, business-focused approach, Amsat helps organizations strengthen their security posture, reduce exposure to cyber threats, and maintain compliance in an ever-changing digital landscape.
Frequently Asked Questions
What is time-to-exploit (TTE)?
Time-to-exploit is the period between a vulnerability becoming known and attackers actively exploiting it. Short TTE means organizations must act quickly.
What is the signal-to-noise ratio in vulnerability data?
It refers to how many vulnerabilities truly matter versus how many are low-risk. A high signal-to-noise ratio helps teams focus on real threats.
What is cross-domain vulnerability correlation?
It involves analyzing vulnerabilities across networks, cloud, applications, and endpoints to identify shared risk patterns.
How do you identify, assess, and respond to emerging cybersecurity threats?
Organizations use threat intelligence, continuous scanning, risk scoring, and incident response plans to address emerging threats.
What is the difference between threat, vulnerability, exploit, and risk?
A threat is a potential attacker. A vulnerability is a weakness. An exploit is how the weakness is used. Risk is the likelihood and impact of exploitation.
Why is vulnerability management integral to computer security and network security?
It prevents attackers from exploiting known weaknesses, strengthening both systems and networks.
How often should a vulnerability management program scan for threats?
Best practice is continuous scanning or at least weekly, depending on risk tolerance and environment size.
TAGS
- Cyber Security
- Penetration Testing