Latest Blogs
By AMSAT Oct 06, 2023
Top Penetration Testing Tools Every Business Should Know About
Penetration testing (pen testing) is a simulated cyberattack that helps businesses identify and fix security flaws in their systems and networks. A key component of any cybersecurity strategy, pen testing can help businesses secure themselves from real-world attacks.
The market is awash with a wide range of both free and commercial penetration testing tools. Here are some of the most popular pen testing tools:
Nmap:
Nmap is a free and open-source tool for network security assessment and investigation. It supports Linux, Windows, Solaris, HP-UX, BSD variants including macOS, and AmigaOS. Nmap provides both a command-line interface (CLI) and a graphical user interface (GUI).
Penetration testers use Nmap to understand which hosts they can access on a network, what services they expose, which frameworks they are running, and what types of bundled tunnels or firewalls are in use. Nmap can also be used to perform a variety of other tasks, such as:
- Discovering network assets: Nmap can scan a network to identify all of the hosts that are active and listening for connections.
- Checking for open ports: Nmap can scan a network to identify all of the ports that are open on each host. This information can be used to identify potential security vulnerabilities.
- Overseeing network administration tasks: Nmap can be used to monitor network traffic and identify any unusual activity. This information can be used to detect unauthorized access or other malicious activity.
- Observing host uptime: Nmap can be used to track the uptime of hosts on a network. This information can be used to identify hosts that are experiencing problems or that have been compromised.
Wireshark:
Wireshark is a free and open-source network traffic analyzer that can be used to capture and analyze network traffic from a variety of sources, including Ethernet, token ring, loopback, and ATM connections. Penetration testers use Wireshark to investigate security issues on a network, identify potential vulnerabilities, and detect malicious activity.
Wireshark’s graphical user interface (GUI) makes it easy to capture and analyze network traffic in real time. Users can also use Wireshark’s command-line interface (CLI) to modify captured files, apply complex filters, and create plugins to analyze new protocols.
Here are some specific ways that penetration testers use Wireshark:
- Identifying malicious activity: Wireshark can be used to identify malicious activity on a network, such as malware infections, brute-force attacks, and denial-of-service attacks.
- Investigating security vulnerabilities: Wireshark can be used to investigate security vulnerabilities on a network, such as misconfigured services and weak passwords.
- Detecting protocol implementation or configuration errors: Wireshark can be used to detect protocol implementation or configuration errors that could be exploited by attackers.
Wireshark is a powerful tool that can be used by penetration testers to improve their understanding of networks and identify security risks. It is a valuable tool for anyone who wants to improve the security of their networks.
Invicti:
Invicti is a cloud-based and on-premises application vulnerability assessment tool that helps penetration testers find exploitable vulnerabilities in websites. It uses a Chrome-based crawler to scan a variety of web assets, including dynamic web applications, HTML5 websites, and single-page applications. Invicti can also scan authenticated websites by submitting credentials, without the need to configure a black box scanner.
Some of the key features include asset discovery and detection, scheduled vulnerability tests, database security auditing, identification of vulnerable versions of languages and web frameworks, and creation of detailed reports that can form part of a penetration test report.
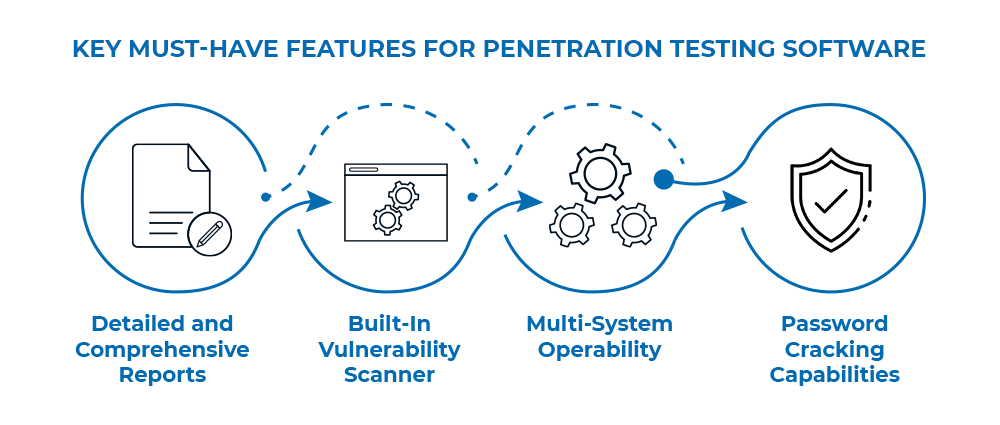
Nikto:
Nikto is an open-source web server scanner that performs comprehensive tests against web servers for over 6,700 potentially dangerous files and programs, outdated software, and version-specific vulnerabilities. It also checks for server configuration issues, such as multiple index files and HTTP server options.
Nikto is designed to be fast and thorough, and it will generate obvious log file and IPS/IDS alerts. However, it does support LibWhisker’s anti-IDS methods for those who want to test their IDS system or evade detection.
Burp Suite:
Burp Suite is a comprehensive application security testing suite from Portswigger that includes the Burp Proxy web proxy. Burp Proxy allows penetration testers to perform man-in-the-middle attacks (MITMs) between web servers and browsers, enabling them to inspect network traffic and identify and exploit vulnerabilities and data leaks in web applications.
Key features of Burp Suite include testing and confirming clickjacking attacks with specialist tooling; assessment of token strength by testing quality of randomness in token data items; deep manual testing; construction of CSRF exploits, making it possible to generate exploit HTML
Hashcat
Hashcat is a powerful password cracker that can crack even the most complex passwords by combining multiple effective methods. Hashcat’s main technique is to manipulate hash keys generated by one-way functions like MD5, SHA, WHIRLPOOL, RipeMD, NTMLv1, and NTMLv2. Hashcat converts readable data to a hashed state and then attempts to crack the password by using a variety of methods, including dictionaries, rainbow tables, and brute force.
In addition to these general-purpose pen testing tools, a number of specialized tools are also available for specific types of pen testing, inclduing wireless pen testing and mobile app pen testing.
Wireless Pen Testing Tools
Used to test the security of wireless networks, wireless pen testing tools can be used to identify vulnerabilities in wireless networks, such as weak passwords, unencrypted traffic, and open ports.
Some of the most popular wireless pen testing tools include:
Aircrack-ng:
Aircrack-ng is a powerful and versatile suite of free and open-source tools that can be used to assess the security of wireless networks and crack WEP and WPA/WPA2 passwords. It includes a variety of tools for packet capture, analysis, and cracking, making it a valuable tool for penetration testers and security researchers.
Aircrack-ng can be used to crack WEP passwords using a variety of methods, including statistical analysis and brute force. It can also be used to crack WPA/WPA2 passwords using a dictionary attack or brute force attack, but this is more difficult due to the stronger encryption used by WPA/WPA2.
Kismet:
Kismet is a powerful and flexible wireless network detector and analyzer that can be used to monitor and troubleshoot wireless networks, detect rogue access points, and perform wardriving in real time. It can also be used to collect data for security analysis and research.
A stealthy tool that can be used to monitor networks without being detected, Kismet can also be used to analyze wireless traffic and identify potential security vulnerabilities. It can also be used to collect data for use in intrusion detection systems and other security tools.
Zebra:
Zebra is a comprehensive commercial wireless pen testing tool that includes a variety of features for assessing and exploiting the security of wireless networks. It can be used to perform a wide range of tasks, including:
- Identifying and enumerating wireless networks
- Capturing and analyzing wireless traffic
- Testing the security of wireless authentication protocols
- Detecting and exploiting wireless vulnerabilities
- Generating reports on wireless security findings
Zebra is a powerful tool that can be used by penetration testers, security researchers, and network administrators to improve the security of wireless networks.
Pen Testing Equipment
As well as pen testing tools, businesses may also need to invest in certain pieces of equipment to support their pen testing efforts. Some of the most important pieces of pen testing equipment include:
- Laptop: A laptop is essential for pen testers, as it allows them to carry all of their tools and resources with them. It should be powerful enough to run all of the necessary software, and it should have a good network card for wireless pen testing.
- WiFi adapter: A WiFi adapter is necessary for wireless pen testing. It should be a high-performance adapter that can capture and analyze wireless traffic at high speeds.
- Network tap: A network tap is a device that can be used to capture network traffic on a network segment. This can be useful for pen testers to capture traffic from all devices on a network, including devices that are behind firewalls.
- Man-in-the-middle (MITM) device: A MITM device allows pen testers to intercept and modify network traffic. This can be used to test the security of web applications and other network services.
- Pen testing key set: A pen testing key set is a set of tools that can be used to open locked cabinets and other secure areas. This can be useful for pen testers to gain physical access to systems and networks.
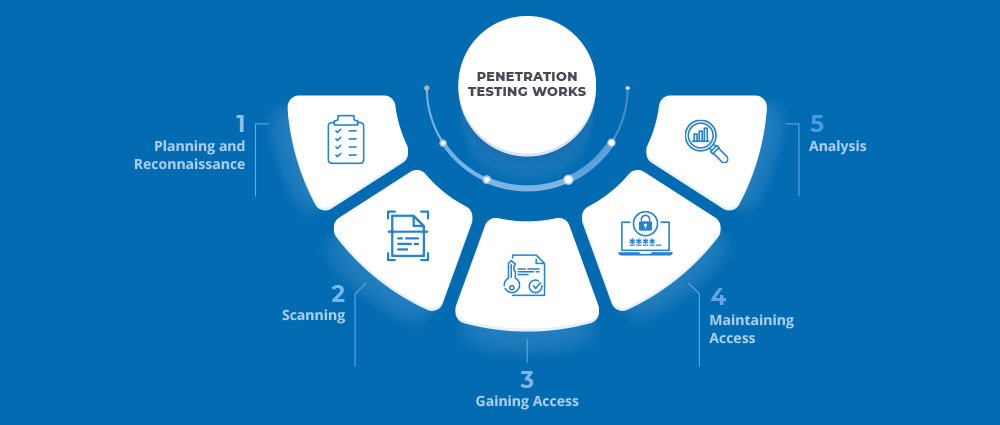
Different Types of Penetration Testing
There are many different types of penetration testing, each with its own focus and objectives. Which type of pen testing is right for an organization depends on its specific needs and goals.
Some of the most common types of pen testing include:
Infrastructure Pen Testing:
Infrastructure pen testing is a comprehensive assessment of an organization’s IT infrastructure. It involves identifying and exploiting vulnerabilities in all aspects of the infrastructure, including networks, systems, devices, applications, and data. Infrastructure pen testing can be performed on-site or remotely, and it can be tailored to meet the specific needs of the organization.
Continuous Pen Testing:
Continuous pen testing is a type of pen testing that is performed on an ongoing basis. This means that the organization’s systems and networks are continuously scanned for vulnerabilities, and any new vulnerabilities that are found are immediately reported and remediated. Continuous pen testing can be performed using a variety of tools and techniques, and it can be automated or manual.
Physical Security Pen Testing:
Physical security pen testing is an assessment of an organization’s physical security controls. It involves identifying and exploiting vulnerabilities in all aspects of the organization’s physical security posture, such as its perimeter security, access control systems, and security cameras. Physical security pen testing can be performed on-site or remotely, and it can be tailored to meet the specific needs of the organization.
If you are unsure which type of pen testing is right for your organization, you should consult with a qualified penetration testing company. They can help you to assess your needs and develop a pen testing plan that meets your specific goals.

Why Businesses Should Use Penetration Testing Tools
Penetration testing tools are essential tools for businesses of all sizes to help them improve their cybersecurity posture and reduce the risk of cyberattacks. By identifying and fixing security vulnerabilities before they can be exploited by attackers, businesses can protect their data, systems, and networks from unauthorized access, data breaches, and other cyber threats.
In addition to improving cybersecurity, pen testing tools can also help businesses to meet compliance requirements. Many industry regulations, such as PCI DSS and HIPAA, require businesses to conduct regular penetration tests to ensure that their systems are secure. By using pen testing tools, businesses can easily and efficiently meet these compliance requirements.
How To Choose the Right Penetration Testing Tools for Your Business
When choosing penetration testing tools for your business, there are a few key factors to consider:
- The type of pen testing you need: Different pen testing tools are designed for different types of pen testing, such as infrastructure pen testing, web application pen testing, or mobile app pen testing. Make sure to choose tools that are specifically designed for the type of pen testing you need.
- The scope of your pen testing: How much of your IT infrastructure do you want to test? If you are only testing a small portion of your infrastructure, you may not need all of the bells and whistles of a full-featured pen testing suite.
- Your budget: Pen testing tools can range in price from free to thousands of dollars. It is important to set a budget before you start shopping for tools.
Once you have considered these factors, you can start shopping for pen testing tools. There are a number of different tools available, so it is important to compare different options before making a decision.
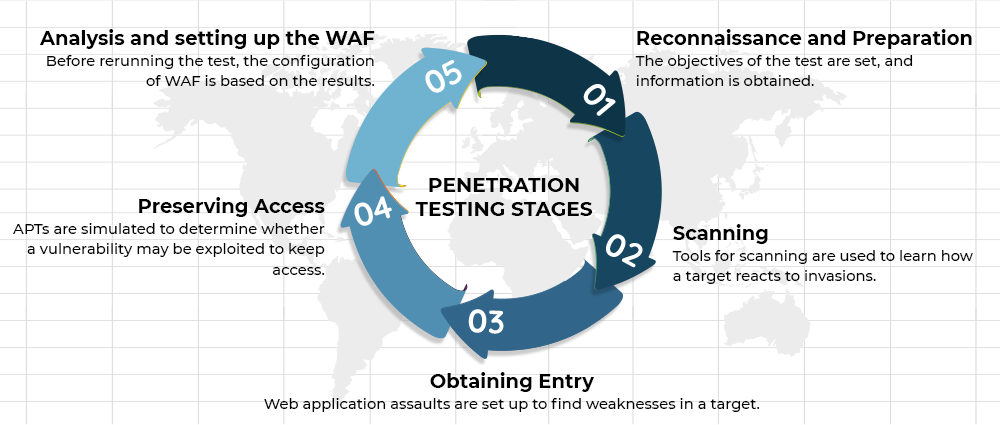
Conclusion
Penetration testing tools play a critical role in strengthening a business’s cybersecurity posture. The tools above are key to detecting vulnerabilities and weaknesses within an organization’s IT infrastructure and applications, and they can help businesses optimize their security assessments.
Not only do effective penetration tools help detect gaps but also enable organizations to remediate these issues, ensuring that they are ever-ready to foil real-world cyberattacks. Needless to say, in today’s fast-evolving landscape of digital threats, these tools are indispensable for outsmarting malicious actors and protecting sensitive data and systems.
TAGS
- Penetration Testing
- Cybersecurity
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.










