By AMSAT November 27, 2025
Agentic AI in Cybersecurity: The Future of Autonomous Defense
Cybersecurity teams are fighting a battle that never really ends. Every day brings new malware variants, phishing campaigns, insider threats, and zero-day vulnerabilities. At the same time, security operations centers, or SOCs, are overwhelmed with alerts, false positives, and tool sprawl. Human analysts simply cannot keep up with the speed and scale of modern attacks.
This is where agentic AI in cybersecurity enters the picture. Instead of AI being just another tool that waits for commands, agentic systems can observe, decide, and act on their own within defined rules. They behave more like digital security analysts who never get tired, never miss a log entry, and can respond in seconds instead of hours.
This guide offers a complete introduction to agentic AI for security leaders, IT teams, and decision makers. You will learn what is Agentic AI, how it works, where it is already being used, how to implement it safely, and why it represents the future of autonomous cyber defense.
What is Agentic AI?
What is Agentic AI in simple terms? It is a type of artificial intelligence that can set goals, make decisions, take actions, and learn from outcomes without needing constant human direction.
Traditional AI in cybersecurity is mostly reactive. It detects a threat and raises an alert. A human then decides what to do next. Agentic AI goes much further.
Key traits of Agentic AI
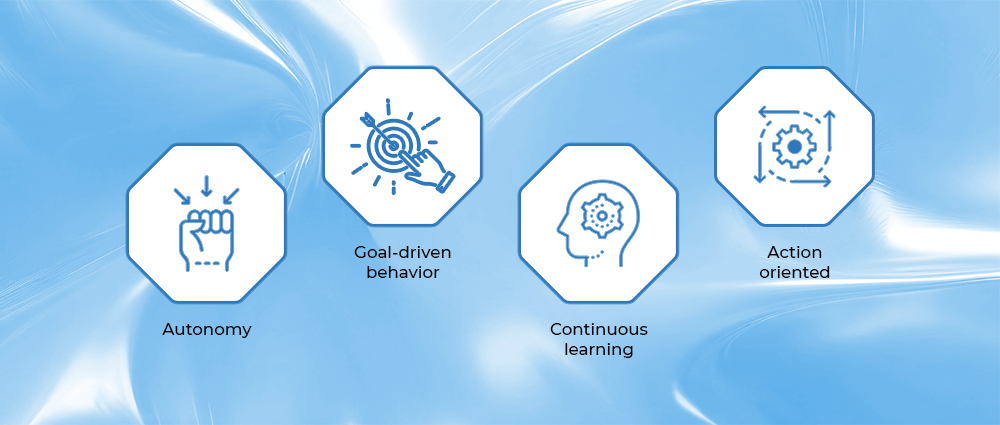
Autonomy
Agentic AI in cybersecurity can decide what action to take based on its understanding of a situation.
Goal-driven behavior
In cybersecurity, when we feed a goal or an aim to AI using machine learning techniques, it works toward specific outcomes such as stopping an attack or reducing risk.
Continuous learning
It improves its decision-making over time.
Action oriented
It is not just a matter of data analysis. It can also perform activities like blocking, isolating, and correcting problems related to threats.
In agentic AI in cybersecurity, these systems are given goals like ‘prevent data exfiltration’ or ‘contain malware outbreaks.’ They then continuously monitor the environment and act to achieve those goals.
This is a major shift from rule-based automation. Instead of following a fixed script, agentic systems adapt their actions as the situation changes.
How Agentic AI Works: Architecture and Mechanism
Familiarizing oneself with the mechanics of agentic AI is one of the key reasons for explaining its power in cybersecurity. Rather than merely responding to warnings when they come in, agentic AI is always there, monitoring silently, contemplating the significance, acting accordingly, and, finally, teaching itself from the feedback received.
On a larger scale, agentic systems are characterized by the circulatory loop of perception, reasoning, action, and learning running continuously. Such a cycle permits the system to be instantly available for and better prepared against threats with every incident it gets through.
Core layers of an Agentic AI system

Each agentic AI system is made up of four main layers that work together to protect your environment.
Perception layer
Functioning similarly to the system’s sensory organs, this layer is in charge of collecting data from various sources, including logs, endpoints, traffic on the network, cloud services, and even threat intelligence.
By pooling information from a range of sources, the AI is able to have a comprehensive understanding of the whole situation across the company’s IT realm.
Reasoning and planning layer
The system’s brain is represented by this layer. It processes the data that is coming in to figure out what is happening now and what might happen next.
It can, for instance, detect anomalous activities, relate them to established attack patterns, and conclude whether or not a genuine threat is evolving.
Action layer
The action layer is activated when a threat is confirmed. It carries out several actions, including blocking dangerous IP addresses, segregating malware-infected computers, or terminating access to a user account that has been hacked.
Such actions are performed automatically and at a very quick pace, thus aiding in the prevention of attacks from doing significant damage through the limitation of their time span.
Learning layer
The learning layer analyzes what transpired once an action was performed. It verifies the efficacy of the response and leverages the knowledge gained to refine the subsequent decisions. In the long run, this makes the agentic AI smarter, quicker, and more precise in the cyber threat management process.
Altogether, these layers allow agentic AI in cybersecurity to function like a smart, always-on digital security analyst that keeps improving with experience.
How this applies to cybersecurity
Imagine a ransomware attack starting in your network.
- The perception layer sees unusual file encryption activity.
- The reasoning layer correlates it with known ransomware patterns.
- The action layer isolates the infected device and blocks lateral movement.
- The learning layer records what worked so it can respond faster next time.
This continuous loop is what makes agentic AI in cybersecurity feel like a living, adaptive defense system instead of a static tool.
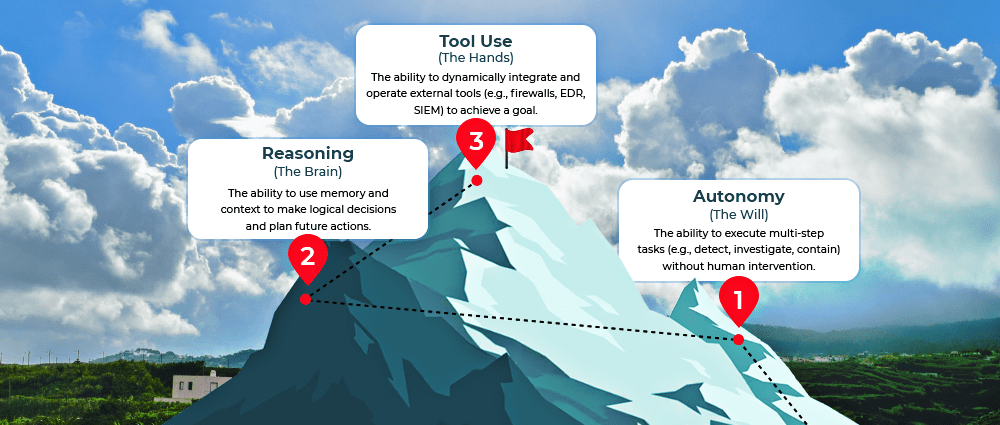
The 3 Pillars That Define Agentic AI Security
Applications of Agentic AI in Cybersecurity
Security is one of the major areas where agentic AI applications are found, and this trend is rapidly gaining momentum as companies are resorting to more intelligent and effective ways of protecting their virtual assets.
The intelligent systems have already been deployed in various high-impact areas, significantly speeding the process of threat detection, analysis, and response with much lesser human input.
Threat detection and triage
Agentic AI has the capability of analyzing at once the minute details of millions of security alerts that are coming from different sources like networks, endpoints, and cloud systems in real time. It can differentiate between actual threats and false alarms and, therefore, it allows security teams to work only on high-risk incidents.
The machines can also take over the human analyst’s job and investigate for themselves, connecting logs and behavior patterns without the need of a human being guiding them through each step.
Incident response
When it comes to incident response, agentic AI can automatically cut off infected endpoints as soon as the detection of malicious behavior occurs thus preventing the malware from propagating through the network.
Compromised credentials can be revoked by the AI to stop the attackers from entering the restricted systems. The AI can also neutralize malicious network traffic by itself, thus making communication between attackers and infected devices impossible.
Vulnerability management
The Agentic AI tool will always be on the lookout for vulnerabilities in the systems, applications, and cloud workloads, and it will do this through constant scanning of these areas. It will categorize the vulnerabilities according to the risk for the real world, and it will consider the likelihood of the exploit, the importance of the system, and other such factors.
Then, the system will be able to initiate the patching or change in configuration to lower the risk, and it will do this without waiting for manual approval in the case of a low-risk situation.
Cloud and identity security
In the areas of cloud and identity, the agentic AI will be watching over the unusual login behavior and will be using it as a sign of account compromise. The AI will be performing a risk assessment of the login behaviors done by different users based on the analysis of various factors such as device fingerprints, and geographic login locations, as well as access patterns.
In situations where the risk is assessed to be high, the system can automatically suspend accounts or demand that the user go through an additional authentication process to gain access.
These agentic AI applications significantly reduce the workload on human security teams and close the gap between detection and response, allowing organizations to defend themselves faster and more effectively.
The Benefits of Agentic AI for Security Operations
The benefits of agentic AI go far beyond speed. They change how SOCs operate.
Faster detection and response
According to IBM’s Cost of a Data Breach report, organizations using AI and automation reduced the data breach lifecycle by an average of 108 days compared to those without these technologies . Faster response means less damage.
Reduced analyst burnout
Agentic AI significantly reduces the mental and operational load on security analysts by handling repetitive and time consuming tasks automatically. This allows teams to work more efficiently and avoid the fatigue that often leads to mistakes or missed threats, which means:
- Fewer false positives.
- Less manual investigation.
- More focus on strategic work.
Continuous 24/7 defense
Agentic AI provides nonstop protection by monitoring systems around the clock without breaks or slowdowns. This ensures that threats are detected and handled immediately, even outside normal business hours.
Agentic systems do not sleep, take breaks, or miss alerts during night shifts, weekends, or holidays, making them ideal for protecting globally distributed IT environments.
Better consistency
Agentic AI applies security policies and response actions the same way every time, regardless of how busy or stressful the situation becomes. This eliminates the variability that often comes with human decision-making under pressure.
They apply the same high-quality response to every incident, helping organizations avoid costly errors, overlooked threats, or delayed actions during critical security events.
The 4-Step Roadmap to Agentic AI Implementation
Implementing agentic AI in cybersecurity requires a structured approach. Breaking it down into clear steps ensures a smooth rollout and maximum effectiveness.
Step 1: Define the Scope
The deployment of agentic AI must be done by starting small and concentrating on the specific issues that have the highest impact. The choice of use cases determines the quickness with which the system can provide visible results.
What to do:
- Pinpoint critical areas where the human analysts are swamped or response times are very important, such as phishing investigation, malware monitoring, or detection of unusual logins.
- Pick cases with very clear expected results so that the performance of AI can be evaluated very well.
- Create objectives that can be quantified like the reduction of the time taken for the detection of incidents, decrease of false positives, or the increase of the number of alerts that have been automatically resolved.
By limiting the scope, the organization has the possibility of implementing agentic AI in cybersecurity through a controlled environment. It is then easier to validate the results, modify the workflows, and show early success before moving on to larger or more complicated use cases.
Step 2: Establish the Guardrails of Security & Governance
While agentic AI can still perform completely by itself, it still has to work within strict limits that are defined in order for it to be safe and compliant. The guardrails that are put in place are the ones that prevent any unintended actions that might cause a disturbance in business operations or lead to the emergence of new security risks.
Key controls:
- You should enforce role-based access control so that only the actions of the AI that are authorized get to be carried out.
- Moreover, you can create approval workflows for the actions that involve a high risk, like cutting off the network or locking the account.
- Also, you will need to keep very thorough audit logs for every single decision and action that the AI performs, which will enable the analysts to go through and get insights from each event.
These guardrails ensure the AI behaves predictably, follows organizational policies, and meets regulatory compliance requirements. They provide confidence that agentic AI in cybersecurity will act safely even in complex, high-stakes environments.
Step 3: Integrate the Toolset (API & Data Access)
Agentic AI can only make intelligent decisions if it has access to the right information. Integration with your existing security tools creates a complete view of your environment, enabling smarter, faster actions.
What to connect:
- SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) platforms for alerts and automated workflows.
- Endpoint detection and response tools to monitor devices for malicious activity.
- Cloud services and identity providers to track access patterns and account behavior.
- Threat intelligence feeds to stay updated on emerging vulnerabilities, malware signatures, and attack trends.
By connecting these data sources, the agentic AI system gains context and situational awareness, allowing it to make better decisions and respond more effectively to threats.
Step 4: Human-in-the-Loop Validation & Scaling
Even though the AI possesses all the tools needed for total independence, it is still recommended that the agentic AI work under human control at the very beginning. This adjusting of the machine’s intelligence to the human’s knowledge will create trust, make the machine’s decisions more accurate, and align the organization’s actions with the company’s visions and missions.
Best practices:
- Give human analysts the chance to monitor AI actions and decisions beforehand, especially in critical situations, before fully automating the process.
- The machines’ independence should be gradually increased according to the confidence that was developed in the quality of the AI decision-making.
- Goals, rules, and responses of the system should always be updated according to the knowledge gained from the actual incidents.
This balanced approach ensures agentic AI implementation is safe, reliable, and effective. Over time, it can scale to cover more use cases and operate with minimal human intervention, maximizing its value for security operations.
Challenges and Risks of Agentic AI
The challenges and risks of Agentic AI must be taken seriously.
Security risks
- A compromised agent could act maliciously.
- Poorly designed rules could block legitimate users.
Ethical and legal concerns
- Who is responsible if the AI makes a wrong decision?
- How do you ensure compliance with regulations?
Technical complexity
- Integration across many tools.
- Need for high-quality data.
These risks do not outweigh the benefits, but they demand careful design and governance.
The Future of Agentic AI in the Security Landscape
The future of agentic AI is tightly linked to the growing complexity of cyber threats.
Here’s what the future of cybersecurity and following it’s trends say: Gartner predicts that by 2028, 33 percent of enterprise software will include agentic AI, up from almost zero in 2024, enabling more autonomous digital operations . This trend will reshape how security teams operate.
What to expect in the next few years
- More autonomous SOCs.
- AI agents that collaborate with each other.
- Faster and more precise threat containment.
- Deeper integration with cloud and zero trust architectures.
Agentic AI in cybersecurity will move from an advanced feature to a core part of every serious defense strategy.
Conclusion
Cyber threats are evolving faster than human teams can handle alone. Agentic AI in cybersecurity offers a powerful new way to fight back with speed, intelligence, and autonomy. By understanding what is Agentic AI, learning how Agentic AI works, and following a structured Agentic AI implementation roadmap, organizations can build defenses that are not just reactive but truly proactive.
This is not about replacing human analysts. It is about giving them digital allies that work tirelessly to keep systems safe.
This is where Amsat can make a real difference. As a technology and cybersecurity consulting partner, Amsat helps organizations design, integrate, and deploy agentic AI solutions that fit their real-world security needs.
From selecting the right use cases to integrating AI with existing SOC tools and cloud platforms, Amsat ensures that agentic AI is implemented safely, strategically, and at scale. With the right guidance and execution, businesses can move confidently toward autonomous, AI-driven cyber defense that protects both their data and their future.
Frequently Asked Questions
How is agentic AI different from the automation tools we already use in our SOC?
Traditional automation follows predefined scripts. Agentic AI can reason, adapt, and choose actions based on the situation. It is goal driven, not rule bound.
What specific cybersecurity tasks can Agentic AI automate?
There are various of tasks that you can automate using Agentic AI Automation, but if we’re naming some, here are a few of the best tasks that can make your work infinitely faster if automated:
- Threat detection and triage
- Incident response
- Account lockouts
- Network blocking
- Vulnerability prioritization
How does Agentic AI improve Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR)?
It continuously monitors data and takes action instantly. There is no waiting for human review, which dramatically cuts both detection and response times.
What is the “Future of Agentic AI” in cybersecurity over the next 3 to 5 years?
Expect more autonomous SOCs, smarter agents, and deeper integration with cloud, identity, and zero trust systems.
What are the four core components of an Agentic AI system?
The four core components of an Agentic AI system are:
- Perception
- Reasoning and planning
- Action
- Learning
How does Agentic AI differ from Generative AI (GenAI)?
Generative AI creates content like text or images. Agentic AI focuses on decision-making and action. In cybersecurity, it detects, decides, and responds, rather than just generating reports.
TAGS
- Cyber Security
- Penetration Testing









