Latest Blogs

By AMSAT Mar 05, 2024
Centralize Logs with SIEM for Compliance and Threat Detection
In today’s complex IT landscape, security professionals face a constant struggle: maintaining compliance and detecting threats amidst a sea of disparate data. This data, often in the form of logs, originates from various sources like servers, firewalls, applications, and user activity. Without proper organization and analysis, these logs quickly become an overwhelming burden, hindering both compliance efforts and threat detection capabilities.
This is where Security Information and Event Management (SIEM) emerges as a game-changer. By centralizing logs with SIEM, organizations can transform scattered data into actionable insights, paving the way for efficient compliance and robust threat detection.
SIEM Log Management
SIEM log management goes beyond mere log collection. It offers a comprehensive suite of functionalities, including:
Centralized Log Collection: SIEM acts as a central hub, ingesting logs from diverse sources across the IT infrastructure. This eliminates the need to manage individual log files on each device, streamlining data access and analysis.
Normalization and Parsing: SIEM normalizes the format of collected logs, regardless of their origin. This facilitates easier searching, correlation, and analysis across diverse data sets.
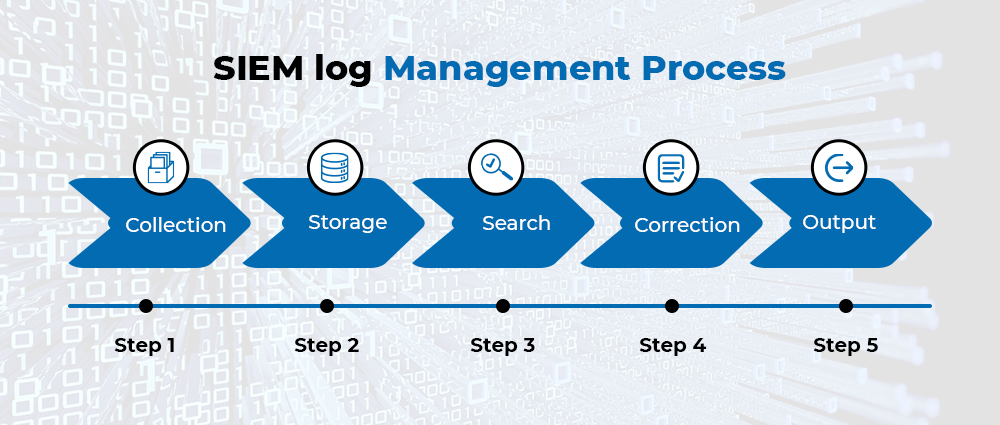
Log Analysis and Correlation: SIEM goes beyond simple storage. It employs advanced algorithms to analyze and correlate log events across different sources. This enables the identification of patterns and anomalies that might indicate potential security incidents.
Threat Detection and Alerts: Leveraging threat intelligence feeds and correlation rules, SIEM can detect suspicious activities and trigger real-time alerts, allowing security teams to swiftly respond to potential threats.
Compliance Reporting: SIEM simplifies compliance by providing consolidated reports on security events and user activity, demonstrating adherence to regulatory requirements.
SIEM and Log Management
While compliance is a crucial aspect, SIEM offers far more significant benefits:
Improved Threat Visibility: By centralizing and analyzing logs, SIEM provides a holistic view of security events across the entire IT environment. This enables security teams to identify and respond to threats more effectively, minimizing potential damage.
Faster Incident Response: SIEM automates alert generation and prioritization based on pre-defined rules, allowing security teams to focus on real threats and expedite incident response times.
Enhanced Security Posture: By providing comprehensive insights into security events, SIEM empowers organizations to identify vulnerabilities and implement proactive security measures to strengthen their overall security posture.

SIEM Log Analysis
SIEM log analysis plays a critical role in extracting valuable insights from collected data. Through various methods such as:
Real-time analysis: Monitoring logs in real-time allows for immediate detection and response to ongoing threats.
Historical analysis: Analyzing historical logs helps identify trends, patterns, and potential security gaps that might not be evident in real-time analysis.
Forensic analysis: In case of a security incident, historical log data can be used for forensic investigation to understand the root cause and identify the attacker’s actions.

By combining these analysis techniques, SIEM empowers security teams to gain a deeper understanding of their security landscape, enabling them to make data-driven decisions and prioritize their efforts effectively.
Conclusion
Centralizing logs with SIEM is an investment that yields significant ROI for organizations striving for both robust compliance and proactive threat detection. By streamlining log management, facilitating comprehensive analysis, and providing actionable insights, SIEM empowers organizations to navigate the ever-evolving security landscape with confidence.
It’s worth noting that effective SIEM log management requires careful planning, implementation, and ongoing maintenance. However, the benefits reaped in terms of improved security posture, faster incident response, and efficient compliance management make SIEM an indispensable tool for any organization looking to secure its IT infrastructure in today’s digital age.
TAGS
- Cyber Threats
- Cyber Security
- SIEM
Recent Blogs
Ready to Get Started?
Our specialists are ready to tailor our security service solutions to fit the needs of your organization.