By AMSAT September 30, 2025
Penetration Testing: Protect Your Systems from Intrusion
Imagine this: you’ve built a strong digital fortress around your business. Firewalls are in place, antivirus software is running, and passwords are updated regularly. You feel confident that cybercriminals don’t stand a chance.
But then, a breach happens. How? Why?
The truth is, attackers are always one step ahead, finding hidden doors and weaknesses most organizations don’t even know exist. This is where penetration testing, often called “pen testing,” comes in. It’s like hiring a friendly hacker to attack your system before the bad guys do.
Here, we’ll break down what penetration testing is, why it’s essential, the types of penetration testing services available, and how it can help you protect your systems from cyberattacks. We’ll also explore the tools, methods, and benefits so you can confidently decide whether your business needs it or not.
What Is Penetration Testing?
Let’s start with the basics. What is penetration testing?
Penetration testing is a simulated cyberattack conducted by security professionals to find vulnerabilities in your system, applications, or network. Think of it as a fire drill, but for your IT security. Instead of waiting for an actual attacker, penetration testers (sometimes referred to as ethical hackers) employ the same tools and tactics that cybercriminals would use, but with the goal of protecting you, not harming you.
The process helps organizations:
- Uncover hidden weaknesses before hackers do.
- Test how well existing defenses hold up.
- Evaluate the effectiveness of security policies.
- Prevent costly data breaches and downtime.
If cybersecurity is a house, penetration testing is the professional who comes in, shakes the doors, tests the locks, climbs the walls, and even tries to sneak in through the basement window, just to make sure you’re safe.
Why Penetration Testing Matters
Here’s the reality: cyberattacks aren’t going away. In fact, they’re increasing in both frequency and sophistication. From ransomware to phishing scams, attackers are constantly looking for a way in.
Relying solely on antivirus software and firewalls is like locking your front door but leaving the back window wide open. Cybersecurity penetration testing ensures that you don’t just have locks in place; you know for sure that they actually work.
Some reasons penetration testing is so crucial:
- Data Protection: Prevent leaks of sensitive customer or company data.
- Compliance: Many industries (finance, healthcare, e-commerce) require regular testing to meet regulations.
- Reputation: Avoid the public relations nightmare of announcing a breach.
- Cost Savings: A single breach can cost millions in damages. Penetration testing services are far cheaper than recovering from an attack.
Types of Penetration Testing Services
Penetration testing isn’t a one-size-fits-all service. Depending on what needs protection, businesses can choose from several approaches. Here are the most common ones:
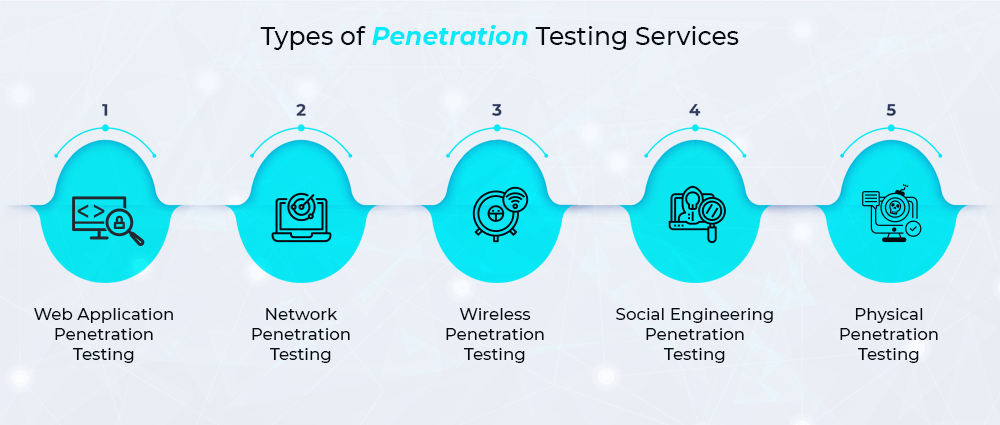
1. Web Application Penetration Testing
Websites and applications are prime targets for attackers. Web application and mobile app penetration testing identifies vulnerabilities such as SQL injections, cross-site scripting (XSS), and broken authentication. These flaws could allow hackers to steal data or hijack user accounts.
If your business runs an online store, customer portal, or SaaS application, web application penetration testing services are a must.
2. Network Penetration Testing
This focuses on your internal and external networks. Professionals simulate attacks to check for weaknesses in firewalls, routers, switches, and connected devices. With network penetration testing services, you can ensure that hackers can’t move freely across your IT environment once they get in.
3. Wireless Penetration Testing
Many breaches happen through poorly secured Wi-Fi. This type of testing identifies issues like weak encryption, rogue access points, and unauthorized devices.
4. Social Engineering Penetration Testing
Sometimes, the biggest weakness isn’t technology, it’s people. Testers attempt phishing, pretexting, or baiting to see how employees react. The results can highlight the need for better training and awareness.
5. Physical Penetration Testing
It may sound like a movie script, but this involves testing physical security controls, like locked doors, ID checks, or cameras, that could allow unauthorized people access to your systems.
A reliable penetration testing company will help you decide which type (or combination) suits your needs.
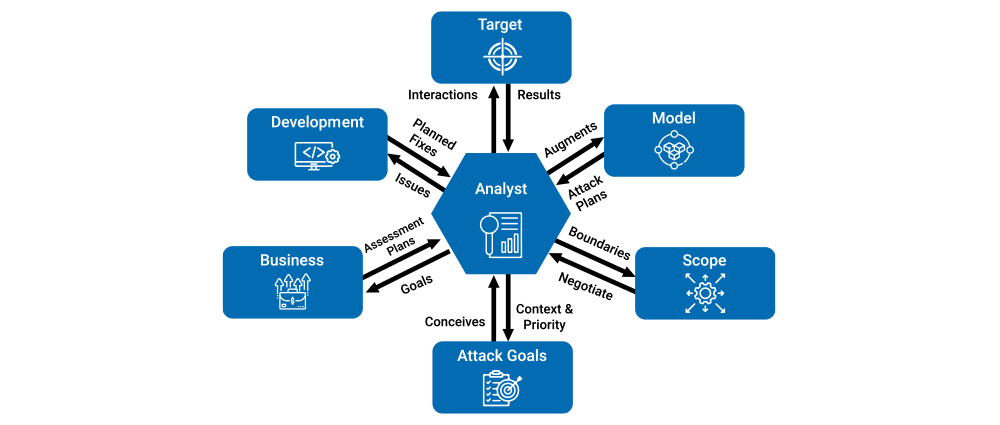
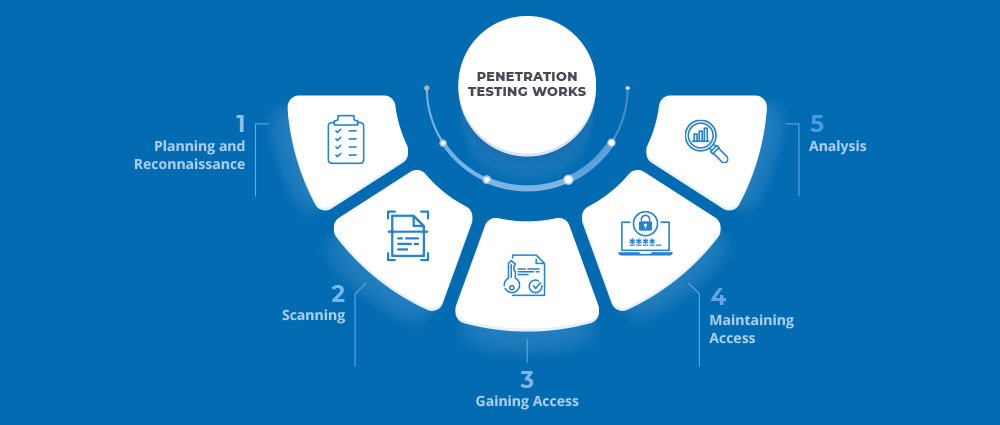
How Penetration Testing Works
The process may sound complex, but let’s break it down into simple steps:
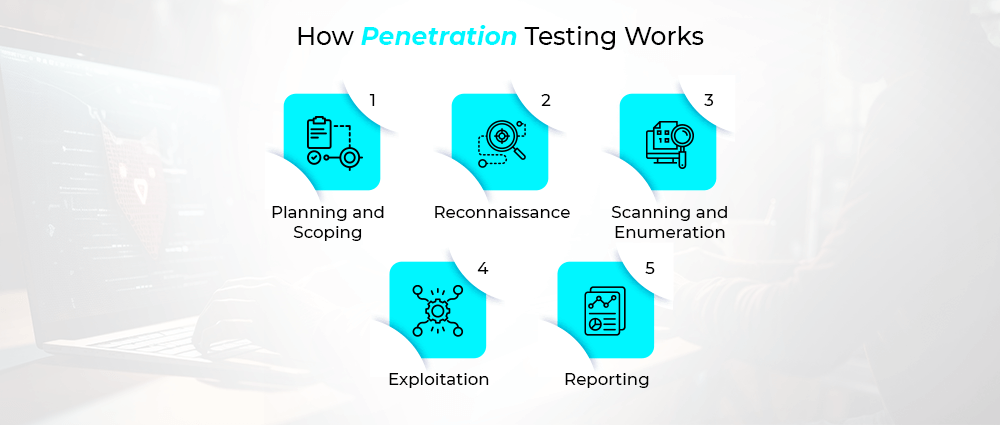
Planning and Scoping
The penetration testing service provider works with you to define objectives. Do you want your web apps tested? Your network? Both?
Reconnaissance
Testers gather as much information as possible about your systems, just like a hacker would.
Scanning and Enumeration
They use penetration testing tools to map your systems and identify potential entry points.
Exploitation
Here’s where the action happens. Testers attempt to exploit the discovered vulnerabilities to see how much damage an attacker could do.
Reporting
Finally, you get a detailed report showing vulnerabilities, the potential impact, and recommended fixes.
This isn’t just a one-time project. Cyber threats evolve, which is why many businesses partner with penetration testing companies for regular checks.
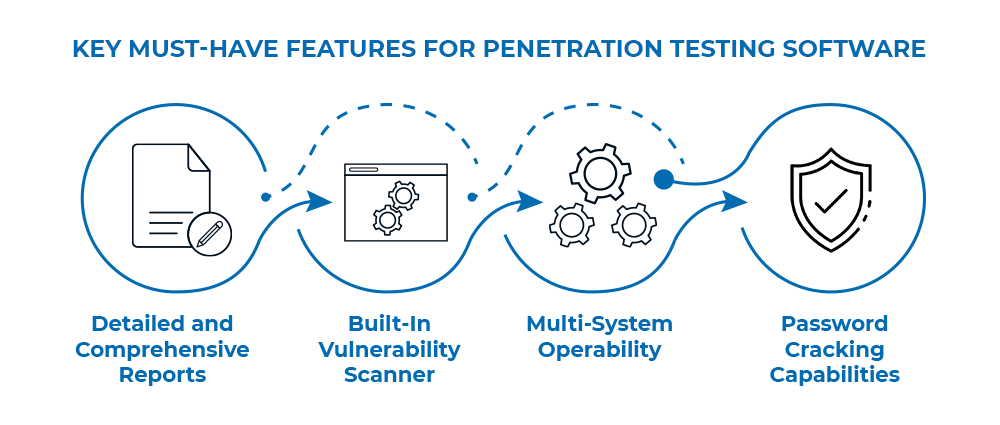
Penetration Testing Tools
Just like a carpenter uses different tools for different jobs, penetration testers use specialized software and frameworks. Some popular penetration testing tools include:
- Metasploit: A widely used tool for exploiting known vulnerabilities.
- Burp Suite: A favorite for web application penetration testing.
- Nmap: Helps map networks and find open ports.
- Wireshark: Monitors and analyzes network traffic.
- OWASP ZAP: Great for automated security testing of web apps.
The right tool depends on the scope of testing, which is why professional services often combine several.
Choosing the Right Penetration Testing Company
With so many penetration testing companies out there, how do you pick the right one? Here are a few tips:
- Experience and Certifications: Look for testers with credentials like OSCP, CEH, or CREST.
- Industry Knowledge: A penetration testing company that understands your sector (finance, healthcare, retail, etc.) will provide more targeted insights.
- Comprehensive Services: Make sure they offer both web application penetration testing services and network penetration testing services, so nothing is overlooked.
- Clear Reporting: The report should be easy to understand, actionable, and not just a list of tech jargon.
A trustworthy partner won’t just hand over findings, they’ll guide you on remediation and long-term improvements.
Common Myths About Penetration Testing
Let’s clear up some misconceptions:
“We’re too small to be targeted.”
Hackers don’t discriminate. Small and medium businesses are often prime targets because they’re less protected.
“We already have firewalls and antivirus.”
That’s like saying you don’t need a doctor because you eat vegetables. Good defenses are essential, but you still need regular check-ups.
“Penetration testing is too expensive.”
Compared to the cost of a breach, lost data, lost customers, regulatory fines, pen testing is an investment, not an expense.
Benefits of Penetration Testing Services
By now, it’s clear that penetration testing is more than just a checkbox on a compliance form. Some key benefits include:
- Proactive Defense: Stay ahead of attackers.
- Risk Prioritization: Identify which vulnerabilities matter most.
- Regulatory Compliance: Meet standards like GDPR, HIPAA, and PCI DSS.
- Stronger Customer Trust: Show clients you take security seriously.
- Continuous Improvement: Regular testing helps you adapt to new threats.
Best Practices for Effective Penetration Testing
If you’re planning to invest in penetration testing, here are a few tips to maximize results:
- Test Regularly: At least once or twice a year, plus after major system changes.
- Cover All Areas: Combine web application penetration testing services and network penetration testing services for full protection.
- Act on Results: A report is only useful if you fix the issues it highlights.
- Train Employees: Use findings from social engineering tests to boost staff awareness.
- Partner With Experts: Work with a reliable penetration testing company rather than trying to DIY with tools.
Final Thoughts
Cyber threats are evolving at lightning speed. It’s no longer enough to rely on traditional defenses and hope for the best. Penetration testing is your chance to outsmart attackers by finding weaknesses before they do.
Whether you’re running a small business or a multinational enterprise, investing in penetration testing services, from web application penetration testing services to network penetration testing services, is one of the smartest moves you can make.
The bottom line? Don’t wait for a breach to expose your vulnerabilities. Get ahead of the curve, partner with Amsat’s highly trained cybersecurity officials to protect your systems, and give your customers the confidence that their data is safe with you.
TAGS
- Cyber Security
- Penetration Testing